Proactive application security is not only essential; it’s needed urgently.
One need look no farther than the staggering 742% growth in software supply chain attacks between 2019 and 2022 to understand that traditional application security (AppSec) solutions are not working.
The core drivers behind this explosive growth in malicious activity are no mystery. On the one hand, adversaries have become more skilled , and the tools used for initiating attacks have become more sophisticated and more easily available. On the other hand Application Security (AppSec) teams find themselves overwhelmed by the complexity brought on by rapid development cycles and the sprawling nature of modern applications, including APIs and cloud environments.
Faced with these challenges, the OX team has dedicated itself to relentlessly pursuing the answer to a fundamental question: Is there a better way? When OX was founded, one thing was already abundantly clear; a systematic, actionable approach is essential for understanding and mitigating attacker behaviors and techniques within the software supply chain.
OX’s vision was for DevOps and AppSec teams to have the ability to not only see, but truly understand the attack paths that adversaries might exploit. This involves adopting an adversary’s mindset to focus resources more effectively, essentially working smarter, not harder. In a landscape where IT systems grow more complex, vulnerabilities proliferate, and securing skilled AppSec personnel is increasingly difficult, OX envisioned a strategy that enabled AppSec teams to differentiate critical vulnerabilities from mere hygiene issues, dramatically enhancing their capacity for targeted risk mitigation. In executing against this strategy, we discovered a crucial layer of data has been missing—one that transforms the approach from using incumbent tools that generate lengthy lists of issues for triage, to a more proactive stance.
The OX Solution: Transforming AppSec with Holistic Insights
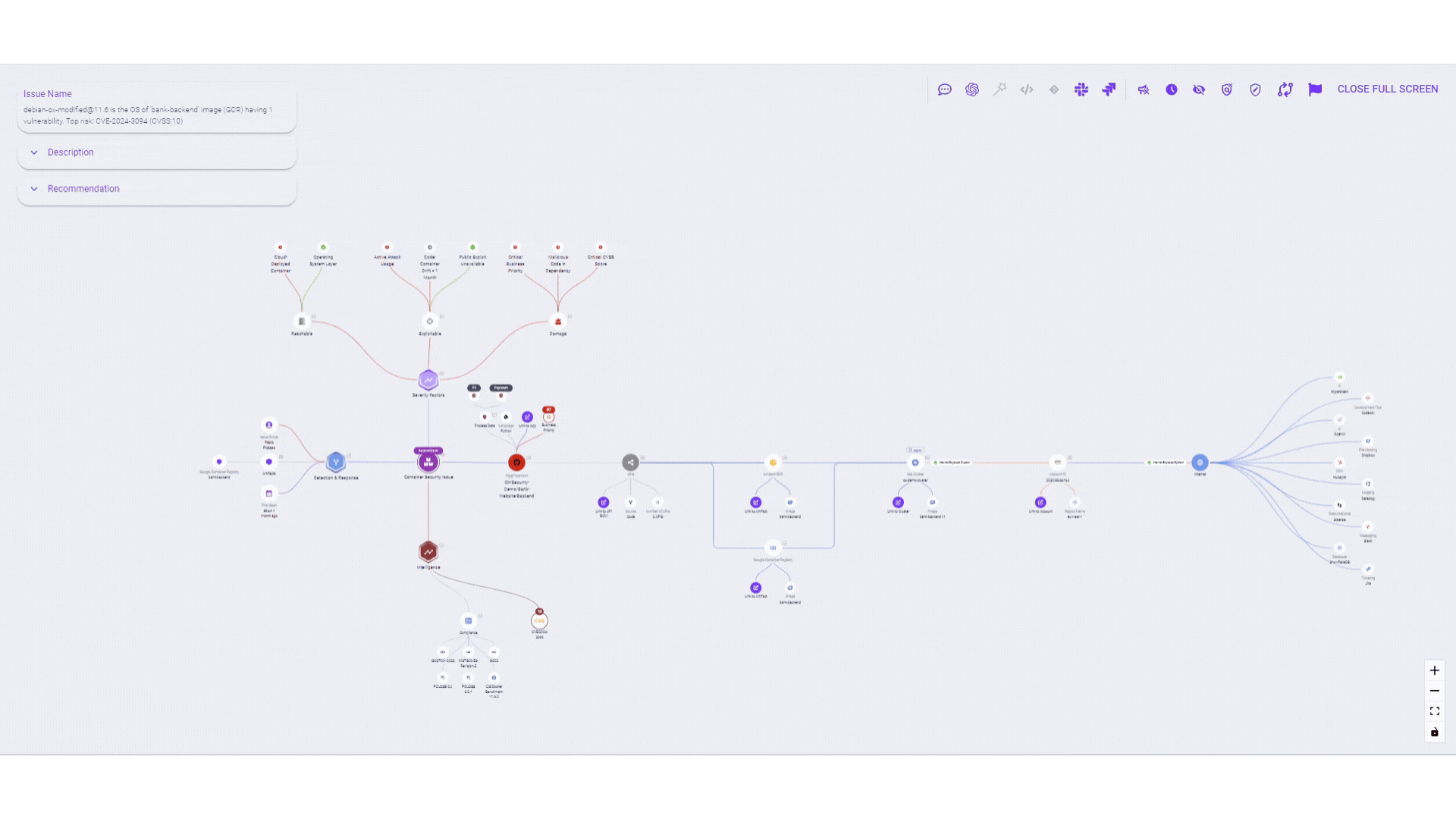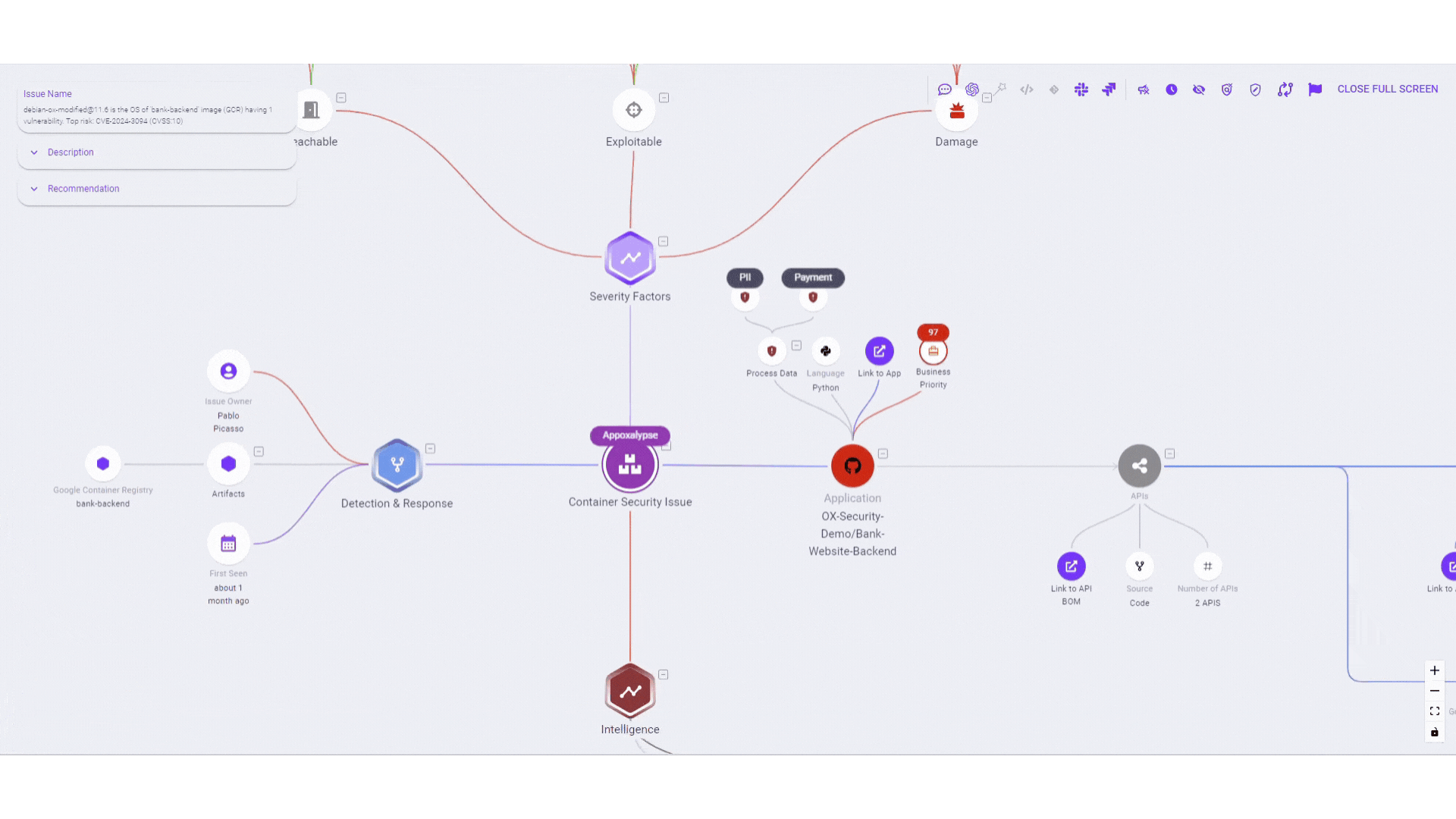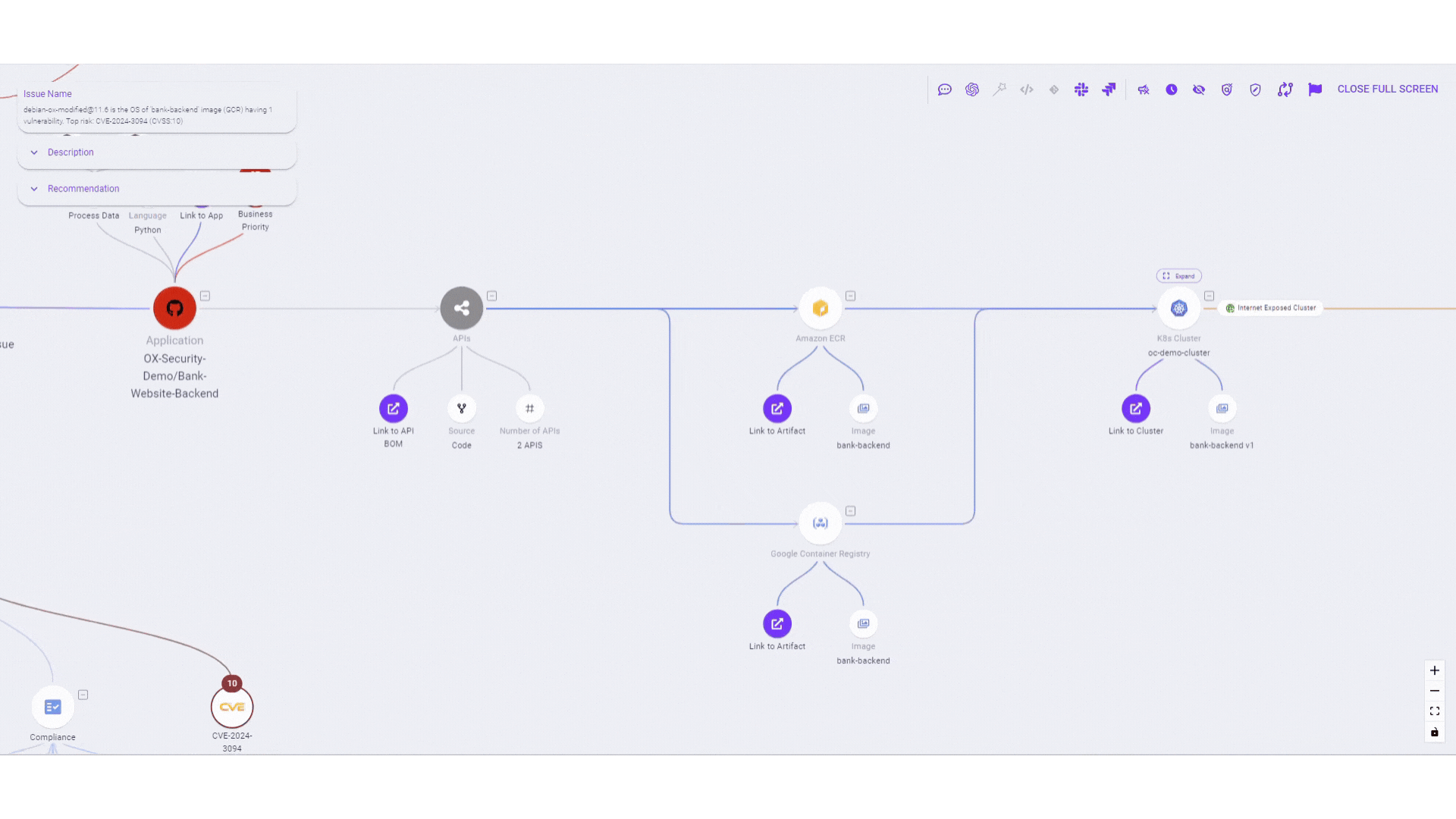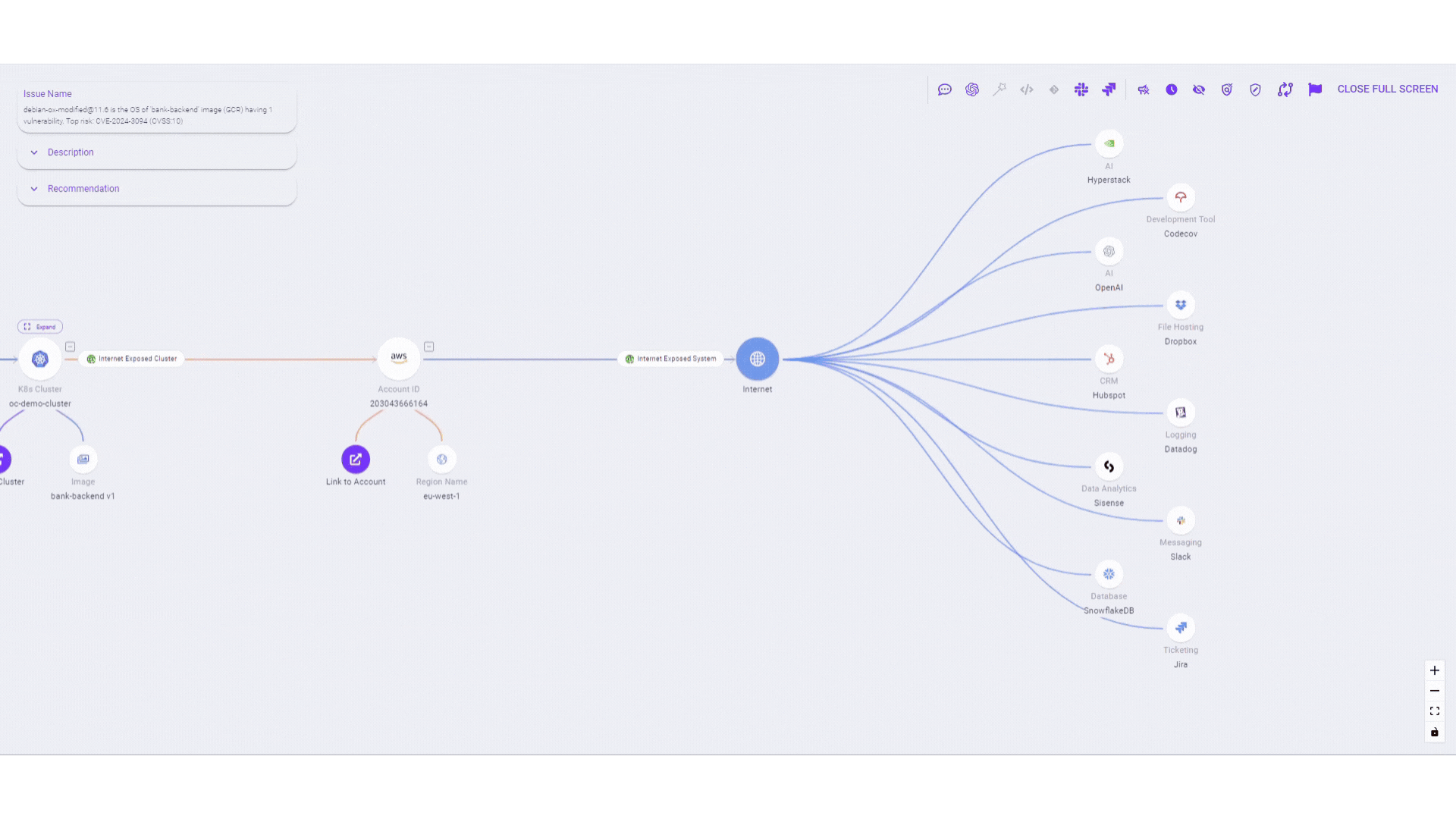
In filling this need, we are over the moon to introduce Attack Path Reachability Analysis within the OX platform, the industry’s first Active Application Security Posture Management (ASPM) solution.
This new feature transcends traditional vulnerability detection and exposure management by providing a comprehensive view of potential attack paths. Whether it’s vulnerabilities in third-party libraries, build system compromises, or tainted software updates, we’re covering all bases from code and API’s to cloud environments. By visualizing these attack paths, users can see through the eyes of an adversary, transforming strategic insights into prioritized, actionable steps
A Closed Loop From Insight to Action
- Comprehensive vulnerability insights: Detailed visualizations dissect potential attack vectors, entry points, data flows, and likely attacker progression, empowering teams to focus on genuine risks rather than theoretical vulnerabilities.
- Holistic issue review: Integrating three tailored levels of security analysis—Code, API, and Cloud—into a unified evaluation, ensuring comprehensive threat identification and assessment.
- Targeted issue prioritization: Proprietary data collection and analysis prioritize risks based on reachability, applicability, and exploitability, directing attention to the most pressing vulnerabilities.
- Efficient cloud monitoring and artifact management: Real-time monitoring and verification of the operational status of artifacts in the cloud enhance overall security posture.
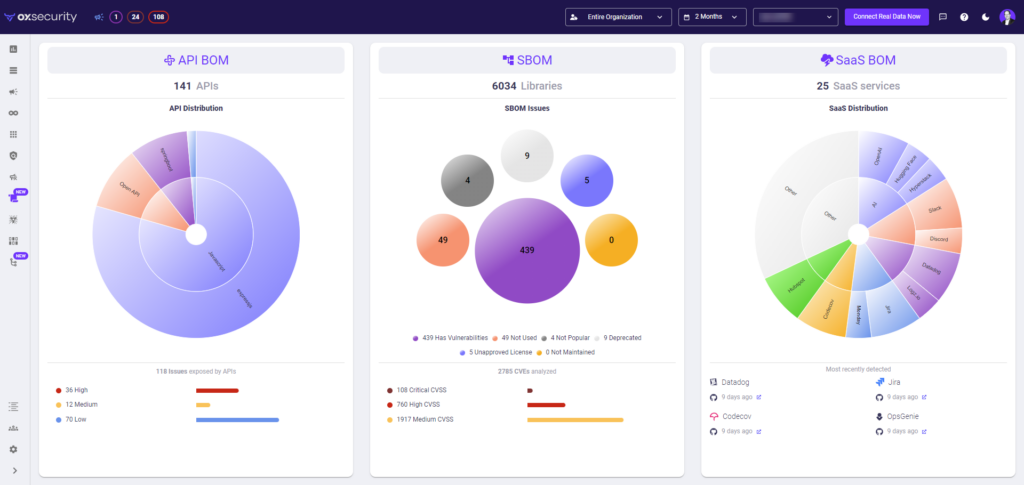
- Detailed understanding of API exposure: A comprehensive view of your application’s exposure through the API BOM (Bill of Materials), empowers you to conduct thorough security reviews by ensuring all APIs undergo rigorous assessments, simplifying the evaluation of newly integrated APIs, and managing high-risk elements of your APIs.
Key Benefits: Complete Coverage and Deeper Analysis
- Secure applications with advanced reachability insights: By integrating code, APIs, and cloud environments with function call graphs, OX uncovers hidden vulnerabilities, securing potential breach points ahead of threats.
- Swift and informed vulnerability remediation: Clarity in crisis is essential. Attack Path Reachability Analysis provides deep insights into each threat’s nuances and severity, streamlining the triage process for swift, informed responses.
- Critical issue prioritization: Distinguishing critical from trivial issues based on reachability, exploitability and impact offers strategic advantages, ensuring that AppSec teams’ efforts are focused, impactful, and timely.
- Advanced third-party incident management: Enhanced BOM capabilities provide a comprehensive inventory of libraries, API usage, and SaaS dependencies, minimizing manual tracking errors and ensuring immediate access to the latest insights.
Looking Ahead: OX Security’s Commitment to Innovating AppSec
Through our latest innovations and strategic partnerships, we’ll continue to redefine AppSec. By building an AppSec data fabric and bringing everything together, we will make sure you have actionable insights and a comprehensive understanding that transforms how organizations protect themselves.
With the launch of the Attack Path Reachability Analysis, we not only address the current challenges faced by AppSec, DevOps and product teams but also anticipate future threats. We’’ continue with the necessary tools to stay one step ahead!
See OX’s Attack Path Analysis for yourself. Book a demo with an expert today!






)

