The reuse of code, libraries, and other software components speeds up development, but it can also introduce security vulnerabilities. Here’s how SBOM tools help.
Most software applications today contain third-party components – as much as 80%, according to some sources – much of it open-source. The reuse of code, libraries, and other software components speeds up the software development lifecycle (SDLC), but it can also introduce security vulnerabilities. Despite widespread awareness, well-known flaws such as cross-site scripting (XSS), SQL injections, and command injections continue to be reintroduced to the software supply chain and therefore challenge organizations’ abilities to effectively tackle software supply chain risk management. There’s a reason why this keeps happening:
Managing software security in accelerated development environments is difficult. Modern applications are complex, with many interconnected components and dependencies. When you’re working at such a rapid pace, the likelihood of vulnerabilities slipping through the cracks is high. And if your AppSec team is already struggling with alert fatigue and supply chain component analysis, triage can quickly become overwhelming. That’s why it’s becoming increasingly important to understand and generate a software bill of materials (SBOM).
SBOM: what it is, why you need it
A lot like an ingredients label for cybersecurity, SBOMs detail all components that comprise a piece of software, including the source code, libraries, packages, and modules in an application – along with their corresponding version numbers, licenses, and other relevant metadata. These insights enable AppSec teams to identify and manage vulnerabilities across their organization’s specific software supply chain. To get to that understanding of the composition of software, a comprehensive SBOM tool is necessary; it mitigates supply chain security risk by providing detailed visibility into the components and dependencies of software.
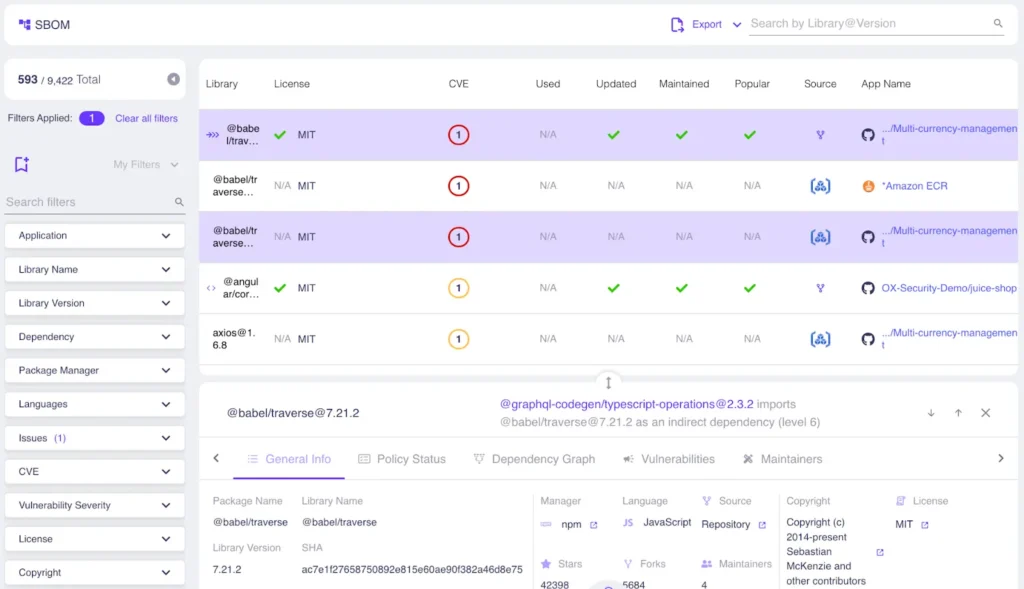
Why does SBOM management matter?
For one thing, SBOM generation became mandatory under U.S. Executive Order 14028 — Improving the Nation’s Cybersecurity, a rule issued in May 2021, the European Union Cyber Resilience Act (CRA), introduced in 2022, and the Cybersecurity and Infrastructure Security Agency (CISA) Binding Operational Directive 23-01. In addition, the U.S. Food and Drug Administration (FDA), Healthcare Industry Cybersecurity Practices (HICP) organization, U.S. Department of Defense, (DOD), U.S. Securities and Exchange Commission (SEC), and National Telecommunications and Information Administration (NTIA) have all issued guidance and strong recommendations for SBOM creation, and in some cases, require SBOMs for software suppliers. The thinking is that SBOMs significantly improve organizations’ abilities to manage software supply chain risk. After all, if you don’t know what makes up your software, how can you be sure of your relative cyber risk?
SBOM generation tools provide defenders with the software composition analysis they need to make informed decisions about software security. Organizations can generate SBOMs with custom-built or commercial-off-the-shelf SBOM generators, or request them from software vendors.
A typical SBOM is created using a standardized format, such as the Open Web Application Security Project’s (OWASP) Software Package Data Exchange (SPDX) or CycloneDX, which is maintained by the Linux Foundation. OX Security’s proprietary Pipeline Bill of Materials (PBOM) standard takes SBOM to the next level, providing a comprehensive list of software lineage, from the first line of code to release, while identifying threats.
Maximizing the benefits of SBOM tools
Some of the ways AppSec and security teams can maximize the data generated by their SBOM tools include:
Streamline vulnerability management: One of the key benefits of SBOM analysis tools is their capacity to enable rapid identification of known vulnerabilities. When AppSec and DevOps teams understand what is in their software and the software supply chain, they can more easily identify where the vulnerabilities are, how those vulnerabilities impact other parts of the software supply chain, and then prioritize remediation efforts that reduce supply chain risk.
Drive Compliance: SBOMs play a significant role in managing software licensing and ensuring all source code is compliant. In addition, SBOMs help organizations meet federal mandates, allowing their software to be used in government agency settings. Similarly, medical device manufacturers are required to have SBOMs as part of compliance with FDA guidelines.
Enhance software supply chain security: The generation and use of SBOMs help mitigate supply chain security risk by providing comprehensive, detailed visibility into the components and dependencies of software.
Effective patch management: Once generated, the SBOM is compared against databases of common vulnerabilities and exposures (CVEs, including those on the National Vulnerability Database), after which threats can be scored and prioritized based on the organization’s needs.
Integrate with CI/CD: Integration with continuous integration/continuous deployment (CI/CD) pipelines makes it possible to generate SBOMs automatically with each software build. This drives enhanced security, transparency, and compliance at every stage of the SDLC.
The benefits are clear but, in many geographies worldwide, generating a comprehensive SBOM has become a key requirement of regulatory compliance for software safety and security.
Compliance, sorted: SBOM mandates
The crucial role played by SBOMs in managing software supply chain risk and bringing visibility into the software supply chain was underlined by the White House Executive Order (EO) in 2021. The EO mandated that software providers to U.S. Federal agencies be able to generate SBOMs for the software they develop. Specifically, the EO stated: “Understanding the supply chain of software, obtaining an SBOM, and using it to analyze known vulnerabilities are crucial in managing risk.”
Organizations with strong SBOM management are better positioned to meet federal mandates, allowing their software to be used in government agency settings. SBOM generation also drives compliance for other sectors, including:
- Medical device manufacturers are required to have SBOMs as part of compliance with FDA guidelines. Many device manufacturers now use software composition analysis tools (SCA) to help with this, for example, an MRI manufacturer could use SCA and an SBOM generator to catalog every component in their device’s operating system.
- Financial services providers could create an SBOM to track all components in trading software and algorithms, in compliance with the European Union’s Digital Operational Resilience Act (DORA).
It’s not just the United States: the European Union’s (EU’s) Cyber Resilience Act, mandates cybersecurity requirements for all products that connect to another device or network and includes responsibility for generating information about software components used and relative vulnerability data.
SBOMs are a powerful tool in the AppSec armory, so it makes sense to understand what to look for in an effective tool.
What to look for in SBOM generation tools
Integrating security into the software development lifecycle is crucial, not only from a compliance perspective, but also as a fundamental component of cybersecurity and operational integrity. With so much at stake, here are some of the key features and factors to consider when choosing an SBOM generation tool:
- Scalability: This is vital in any effective SBOM tool. Modern software projects come with dense networks of dependencies. The most effective SBOM tools can handle projects of varying sizes and complexity without compromising performance.
- Comprehensive integration options: Seamless integration with existing development, security, and operational frameworks is essential. It ensures that SBOMs are automatically updated, aligning component information across the SDLC, and enhancing vulnerability management capabilities.
- Automation: Reduce manual efforts, minimize errors, ensure continuous compliance, and free up time for AppSec and development teams to focus on other important issues. Automated SBOM generation drives all of these outcomes while maintaining up-to-date software inventories that accurately reflect the most accuarte security posture.
- Manageability: If it’s too hard to use, it’s not going to help. Every good SBOM tool has a user-friendly interface and straightforward workflows the help generate information all stakeholders can read and use, regardless of technical expertise.
- Prioritization: Security teams are already struggling with alert fatigue and data from multiple tools. Choose an SBOM tool that helps with resource allocation and addresses vulnerabilities that directly affect an application’s operational security. This will streamline risk management processes and reduce strain on teams.
Let’s take a look at what all of this could mean for organizations’ security strategy.
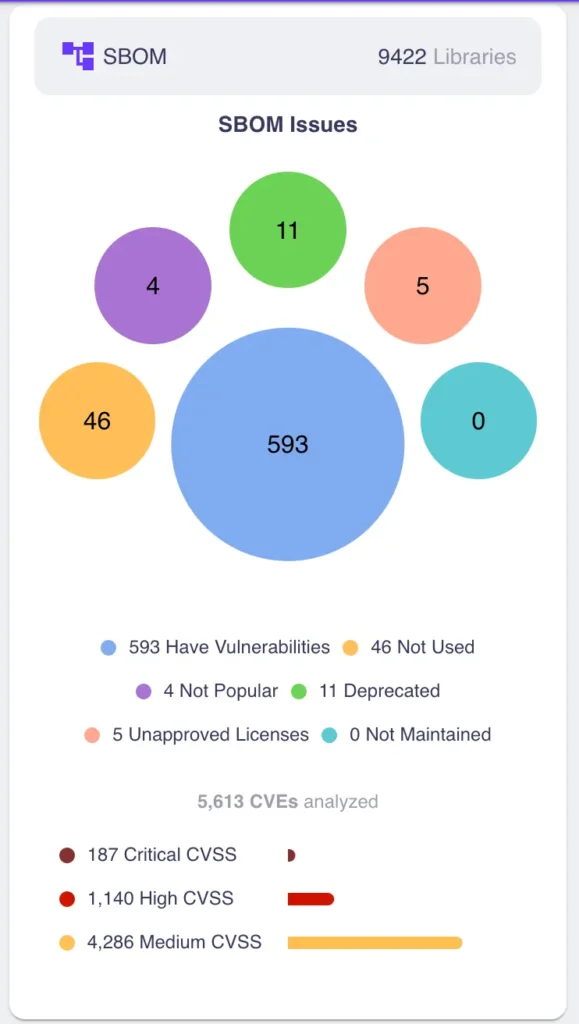
Where SBOM fits in your overall proactive security strategy
We’ve already seen how accelerated SDLCs impact AppSec teams. The ability to trace code to all its sources – along with accompanying vulnerabilities – allows teams to move beyond simple identification and into holistic risk management.
SBOMs empower security teams to adopt a proactive approach to vulnerability management, using the insights generated to mitigate risks before they can be exploited. For example, the clarity gained from insights into specific software components – from third-party to open-source elements – enables rapid identification of the specific parts of software impacted by a newly discovered vulnerability, facilitating highly focused, timely patching. Meanwhile, integration with CI/CD pipelines and other security frameworks facilitates automation, compliance audits, risk assessments, and more.
SBOM management and OX Active ASPM
Ox Security’s Active ASPM Platform includes not only an SBOM generator that creates an SBOM in minutes, but also includes an API BOM, SaaS BOM, and artifacts BOM, for full pipeline visibility. OX gives AppSec and DevOps teams the deep transparency they need, with seamless tracking for licenses, patch status, and dependencies, keeping software supply chain risks to a minimum.
Gain end-to-end SBOM security coverage for your organization, book your demo now!






)


