In recent years, the cybersecurity industry has embraced a “shift left” approach, advocating for security considerations to be integrated earlier in the software development lifecycle. This strategy, born from a desire to prevent security issues before they arise, encourages embedding security checks within the development phase, even as far as the Integrated Development Environment (IDE), where the code is initially written. The logic is sound: identify and mitigate security vulnerabilities early to save time and resources later.
According to the Veracode State of Software Security Report 2024, 45.9% of organizations have critical security debt out of 70.8% of organizations that have security debt. Prioritization is key.
Preventing cyberattack penetration can save enterprises up to $1.4 million per incident, as noted in “The Economic Value of Prevention in the Cybersecurity Lifecycle” by the Ponemon Institute. Sponsored by Deep Instinct, a company that uses neural networks to prevent cyber attacks, the study indicates that the economic value of preventing a cyberattack ranges from $396,000 to $1.37 million, depending on the type of attack.
However, this narrative, while appealing, conceals a more complex reality. As organizations zealously adopt this “shift everywhere” mentality, they inadvertently relinquish control and neglect responsibility for application security (AppSec). The crux of the problem lies not in the philosophy of preemptive security, but in the execution that entrusts developers—who may lack the necessary interest, skills, or expertise—with responsibilities traditionally held by security professionals.
The Unintended Consequences
The pitfalls of an indiscriminate shift-left strategy are manifold. Developers, pressured to prioritize speed and functionality, may find themselves ill-equipped to navigate the complexities of AppSec. Integrating security tools directly into IDEs, while seemingly a step forward, often leads to a deluge of false positives. These inaccuracies not only erode developers’ trust in security tools but also hamper productivity as they sift through irrelevant alerts. This situation is compounded by a loss of visibility for security teams, who find themselves unable to monitor, prioritize, and ensure the remediation of genuine vulnerabilities effectively.
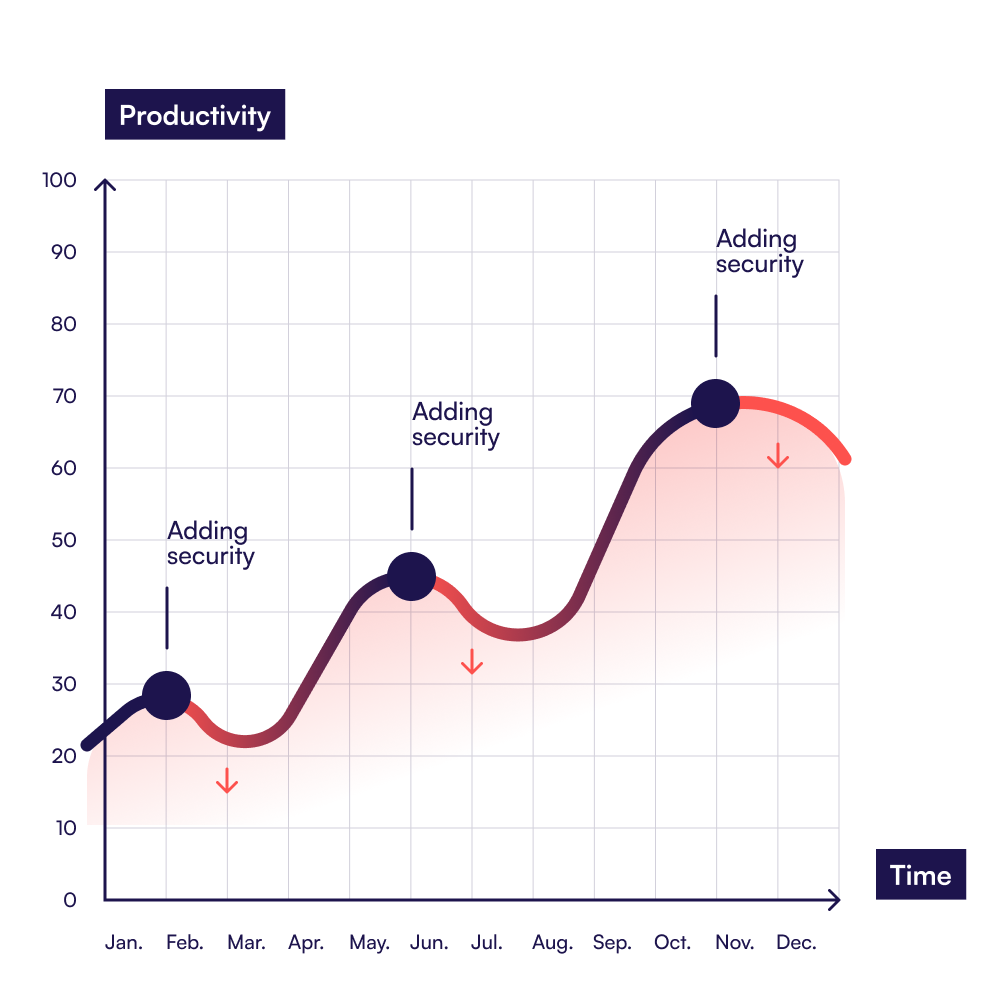
The graph above illustrates this issue. The red line shows a sharp decline in productivity at the point of adding security, with a slow recovery afterward. The ideal scenario will be adding security responsibly and maintaining a steady productivity level.
The Balancing Act
The challenge, then, is not to refute the value of shifting left but to discern the extent and manner of its application. The integration of security within the Continuous Integration/Continuous Deployment (CI/CD) process and at the build or merge stage offers a more nuanced approach. At these junctures, the context of security issues is clearer, enabling more accurate identification and prioritization of genuine risks. Nevertheless, this integration must be approached with caution to avoid inundating developers with false positives that foster friction and distrust, leading to security measures being ignored or bypassed altogether.
A Strategic Reorientation
The key to effective AppSec lies not in the abandonment of shift-left principles but in their strategic application, complemented by a robust framework for visibility, control, and prioritization. Before diving into IDE or commit-time integrations, organizations must ensure comprehensive coverage of the application pipeline, contextual prioritization of threats, and the automation of response and remediation processes. This approach allows for the advantages of early security integration—such as reduced risk and enhanced efficiency—without the drawbacks of lost control and increased business risk.
Laying the Foundation
To navigate this paradigm shift, organizations must first outline a clear process for achieving complete application pipeline coverage. This includes the integration of security controls and platforms throughout the development and deployment phases, ensuring that security teams can maintain oversight and intervene when necessary. Contextual prioritization of vulnerabilities is crucial, enabling the focus to remain on threats that pose the greatest risk to the business. Finally, the automation of response and remediation processes is essential, allowing for swift and efficient handling of security issues without overwhelming development teams.
This comprehensive approach repositions security decision-makers to reclaim control over AppSec, shifting the narrative from one of abdication to one of empowered responsibility. By balancing the benefits of early security integration with the need for oversight and expertise, organizations can enhance their security posture without compromising the efficiency and innovation at the heart of software development.
Stay tuned for part two.
Interested in shifting to early security integration and achieving comprehensive pipeline coverage without compromising development efficiency? Click Here.