Analyst firms play an important role in the tech vendor landscape. Their reports help buyers and would-be buyers learn about vendors and their offerings. In cybersecurity, in particular, buyers use analysts’ outputs to build shortlists prior to thee kick-offs of their individual deep dive evaluations — in some categories of tools, the field is simply too big for end users to wade through the crowded waters and identify the top two (or ten) vendors and functionality suitable for their needs.
But this is where things start to get tricky. There is no one-size-fits-all when it comes to tech deployments. The good analysts will tell you that each buyer organization runs on different priorities, needs, goals, internal resources, risk tolerances, business drivers, mission- and business-critical information and systems, maturity levels, and so on. All these things, combined, necessitate customized IT infrastructure and architecture, not to mention, tailored configurations, alerts, etc. What this means is that there is no “best” when it comes to cybersecurity technology. Best is subjective.
Furthermore, the very fabric that makes up the cybersecurity vendor landscape — all the companies, all the categories — is shifting all the time. Some of this shift is predicated on technology advancement and market dynamics. Take large learning models (LLMs), for instance. Recent improvements in the technology are rapidly shaping how vendors are building and upgrading their products. As a result, new categories of technology are emerging that LLMs can be hardened to attack.
New tech to tackle the application attack surface
Moving back, closer to home, application security is advancing year upon year upon year. Applications have become so deeply entrenched in day-to-day business that they’re as essential as turning the lights on when it’s dark. The number and breadth of in-use applications at any one business is astounding, and so much of the development work — work that used to be outsourced to a few, select specialists — has significantly moved in-house and is managed by large, multi-talented teams. Even seemingly simple applications are actually highly complex, interconnected ecosystems of components with hard-to-track dependencies and (sometimes) hidden but long standing vulnerabilities. And all this makes the speed of development hard for security professionals to keep up with.
Yet the threats to applications increase continuously, which means that vendors like OX are innovating all the time. New capabilities are required to combat software complexity, speed, and the growing application threat landscape. New, automated analysis tools that incorporate functionality such as enhanced data and logic flow analysis, symbolic execution, seamless integration with CI/CD pipelines, false positive reduction, contextual enrichment, dependency mapping and analysis, and more need to be part and parcel of today’s tools.
Application Security terminology confusion
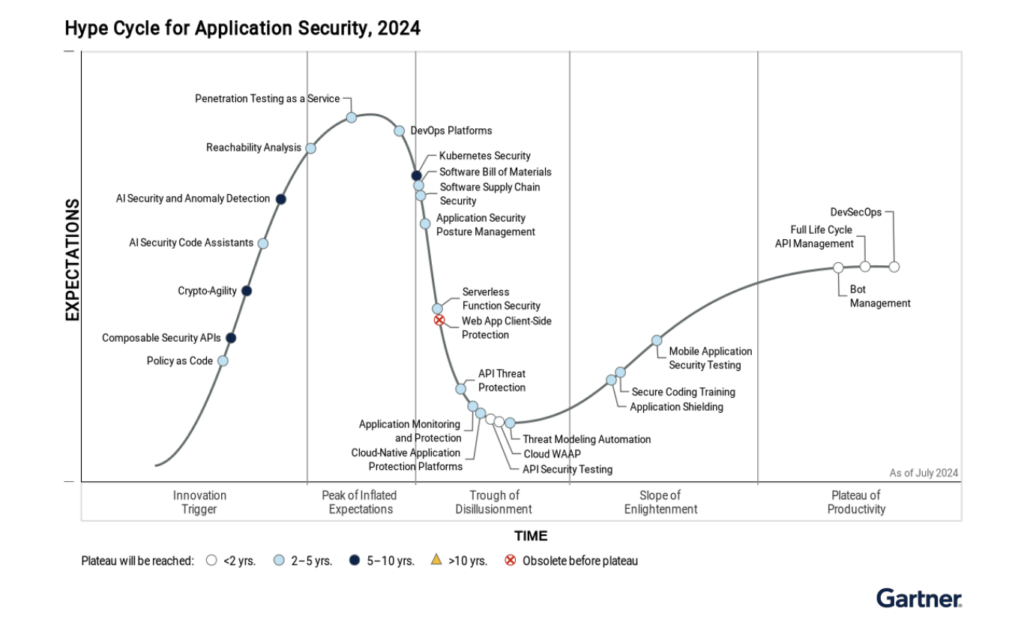
But here’s the problem: As the application landscape has evolved, and the application attack surface has grown alongside it, different types of tools have been invented. As per usual, category creation started off small in the early days but has now exploded. One look at the newest Gartner Hype Cycle for Application Security, 2024 shows you everything you need to know about the explosion of AppSec terms.
Source: Gartner
Terms like “Application Security Posture Management,” or “ASPM” in its acronym form, are rather new. OX Security is listed (appropriately) as a sample vendor in ASPM in the Hype Cycle for Application Security as well as in the Hype Cycle for Open-Source Software, 2024.
However, in Gartner’s Market Guide for Cloud-Native Application Protection Platforms (CNAPP), OX Security is listed as a sample vendor in Software Supply Chain Security (SSCS). This is a somewhat older term (though not antiquated by any means), and OX fits squarely into this category as well. Yet, while OX is categorically not a CNAPP, many of the requirements for CNAPP listed by Gartner, are, indeed, capabilities of the OX Active ASPM Platform. Things are starting to get confusing. (And I work here.)
Continuing on, in the firm’s Emerging Tech Impact Radar: DevOps, OX is also listed as a sample SSCS vendor but not an ASPM vendor. And in their Gartner for Software Engineering Leaders Tool: Create a Customer technology Roadmap for Software Engineering presentation, OX security is listed as a sample vendor for secure code assistants and software bill of materials (SBOM). In fact, OX not only offers SBOM coverage, but API BOM and SaaS BOM, too. The term “secure code assistant” is interesting because it seems to bundle a number of capabilities offered in the OX and like companies’ solutions. Per Gartner’s report:
Source: Gartner
This term, then, covers a lot of ground, as it encompasses a variety of testing tools, some of which would otherwise be categorized in vastly different budgeting buckets by enterprise buyers. Just trying to keep track of terms is tricky, nevermind trying to determine where certain vendors fit. It becomes especially complicated with a company like OX that combines related elements into one platform. We’re hardly alone in this approach.
When like-sounding tools are put in inconsistent categories by third parties that are supposed to be disambiguating markets, and the vendors, themselves, use multiple categories to cover varying components of a suite, how are buyers supposed to make sense of it all? Now, in all fairness, categories like SBOM and secure code assistants are not the same and likely won’t be confused with one another. It’s easy to see how and why differing vendor offerings would fall into these two categories. But when it comes to categories like ASPM, SSCS, DevSecOps tools, application protection platform, and the like, it might make sense to consolidate terminology.
We can’t speak for anyone else, and this post won’t have any impact on how others categorize OX, but in an effort to clarify what ASPM and SSCS mean in OX’s terms and why the OX Active ASPM Platform fits into both ASPM and SSCS, and also qualifies as a solution for SBOM, secure code assistant, and several other AppSec slices.
What is ASPM in OX terms?
Imagine your software development process as an assembly line for building a car. Parts are constructed (developed) and assembled at various stations, in a certain order. Now, in some cases, parts are not build in the factory where the car is assembled. Maybe they were shipped form another factory owned by the manufacturer. Maybe they were built and shipped from a third-party factory in a foreign country. Regardless of where the parts were build, each needs to be assembled on this current line, and a quality control inspoector need to ensure everything fits together correctly and securely.
ASPM is like the quality control inspector on the app assembly line (which, in this analogy, is the CI/CD pipeline). It continuously checks for defects and weaknesses throughout the entire process, from design (development) to final assembly (deployment).
The “quality control inspector” continuously monitors applications throughout their journey on the “assembly line,” gathering information from a collection of sources, and reporting on what needs to be fixed. In the ASPM world, these technology categories and processes include all the “AST”s like SAST, DAST, and IAST; software composition analysis (SCA), to help teams understand which elements comprise the software; infrastructure as code (IaC) elements; and container environments.
ASPM is the key to visibility, prioritization, contextualization, and remediation.
- Visibility: When dev teams build applications, security issues are not always readily apparent, and can get added to the “assembly line” at various stages of the build. ASPM gathers and inspects information from all stages, providing a clear picture of app’s overall security.
- Prioritization: Not all security issues are created equal. ASPM helps identify the most critical problems first, so dev or security teams can fix the most critical risks first and fast.
- Contextualization: ASPM provides not just insights about the components, but details on why, where, and when, making it easier for developers and security teams to understand business impact and what needs to happen next.
- Remediation: ASPM doesn’t just point at problems and say, “take it off the assembly line!” Unless the threat is apocalyptic, few organizations are going to shut down an app entirely for a fix. ASPM offers up detailed recommendations and automated response actions so the assembly can keep running smoothly.
The benefits of ASPM — when done well — include a faster time-to-market, improved software/application quality, increased efficiency, better collaborate between teams, and a lower risk of errors and failures.
What is software supply chain security (SSCS) is OX terms?
Continue to imagine the software development process as an assembly line. SSCS is like a security guard for that line, ensuring only safe and authorized components are used. It includes tools, processes, and strategies to protect software, starting at the time of creation (development) through its final use (deployment).
In the case of SSCS, the “security guard” inspects everything from overall code, Git, container, and cloud environment posture; all the way down to the artifacts used; the entiresoftware bill of materials (SBOM); secrets like passwords, API keys, encryption keys, database credentials, and certificates that ensure secure access to code and coding environments; transitive vulnerabilities and dependencies; as well as other important software hygiene and operational-state information that helps security and development teams assess and triage risk.
Like ASPM, the SSCS market is young but growing rapidly, with many new entrants at every turn. Because software supply chain attacks are so prevalent, businesses are hyper-aware of the risks. Further, countries are increasingly passing regulations that require greater attention to and stronger protection for software.
SSCS is a complement to ASPM, acting as the watchguard for the software assembly line, helping security and dev team to:
- Reduce Risks: SSCC is always on the lookout for threat actors trying to inject malicious code into software, change configurations, abuse permissions, and generally stop deviant behavior.
- Maintain Integrity: SSCS ensures that applications are running as intended and expected by the developer; and don’t contain vulnerabilities, backdoors or other unauthorized modifications.
Simplifying ASPM and SSCS adoption
Not surprisingly, the assembly line and its impsectors can easily get overwhelmed. That’s because many vendors claim feature parity (despite the clear presence or absence of various “assembly line” tools), the definitions of various categories can be conufsing and/or conflicting, and because both new categories are being built from earlier generations of AppSec tools. The add-on approach leads to certain solutions with components bolted on — like aftermarket parts — instead of been built into the initial design.
Fragmented tools and confusing definitions make it hard for buyers to understand what a true, holistic ASPM and SSCS platform looks like. The OX Active ASPM Platform is purpose-built for modern software development, and its design is predicated on a data fabric that ensures the assembly line is running smoothly and that the security guards have all the right data, information, and capability to fund and fix ocnfidentiality, integrity, or availability issues in applications — and throughout their entire lifecycle.
While we can’t fix the categorization issues that plague the industry, we can assure you that OX has your AppSec covered. As application security evolves, so too will our platform. Third-party waqtchers might add OX to new or different categories. Others might decide to remove us from old categories for whatever reason. We can’t tell what will happen in the ever-changing world of security category hype, but we can promise we’ll help make your development “assembly line” safer, more secure, and easier to manage
Boost your AppSec with advanced strategies; request a demo to see how it works.