Over the last few years, containers have emerged as a cornerstone technology, enabling scalability, efficiency, and consistent environments across development, testing, and production. However, the rise of containers has also introduced new security challenges, particularly around managing vulnerabilities that can compromise the entire application stack.
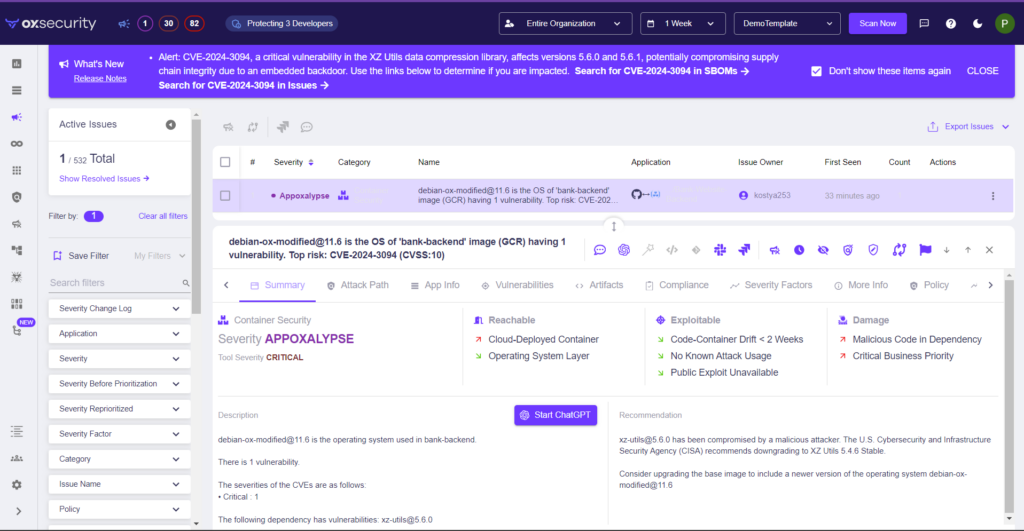
By now, you’ve heard about the discovery of malicious code embedded in XZ Utils versions 5.6.0 and 5.6.1, identified under CVE-2024-3094. Given XZ Utils’ widespread usage for compression and decompression in Linux distributions, the vulnerability primarily threatens container images rather than user-side code. This incident underscores the critical importance of container security/scanning in conjunction with active application security posture management (ASPM) in safeguarding against such vulnerabilities.
Bridging the Gap with Contextual Analysis
One key advantage of integrating Container scanning with your AppSec practices is the ability to perform contextual analysis. This process links container vulnerabilities directly back to the source code, shedding light on where a problem lies, who introduced it, and how it can be effectively remediated. By creating a direct linkage between container issues and source code vulnerabilities, organizations can bridge the gap between container security and code-level issues, making vulnerabilities more actionable and remediation more precise.
Streamlined Triage and Prioritization
Containers, by their nature, inherit severity factors and other attributes from their corresponding code repositories. This relationship allows for a more nuanced assessment of risk, factoring in elements such as container drift, the usage of vulnerable functions, and the overall impact of the issue. Additionally, with Active ASPM there users access reachability analysis which allows the platform to understand that a container is deployed and create an attack path from cloud to code. As a result, prioritization is based on a comprehensive visibility into the vulnerability context, including its origins in the code. This streamlined approach to triage and prioritization ensures that efforts are focused on the most critical vulnerabilities based on their severity and the context in which they exist.
Automating the Response to Vulnerabilities
Integrating Container scanning with Active ASPM offers a clear path from vulnerability identification to resolution, enabling organizations to automate the triage and prioritization process. Automation in this context covers determining where fixes need to be applied, who is responsible for them, and the specific actions required to remediate issues. This level of automation significantly reduces manual effort, accelerates response times, and enhances the overall security posture of the application stack.
Addressing Key Challenges
Manual Triage Work
Traditionally, identifying a vulnerability within a container involved an extensive manual effort to trace it back to its source code origins. This proved time-consuming and often required more precision to understand the issue’s true severity and context fully. The integration of Container scanning addresses this challenge by providing an automated, accurate linkage between container vulnerabilities and the corresponding source code, enhancing both efficiency and efficacy in vulnerability management.
Actionability of Issues
Security tools often overwhelm users with many issues that need actionable insights. This is particularly true for vulnerabilities that are part of a base image and not directly tied to the application code. By establishing a direct connection between container issues and the code, vulnerabilities evolve from alerts to actionable items with clear paths to resolution, enhancing the actionability of security insights.
Siloed Security Practices
The complexity of containers extends beyond technical challenges, as multiple teams contribute to the code: from DevOps, who build the base image and provide user instructions, to developers, who commit the application code, underscoring the multifaceted nature of container security.
Despite this container security has traditionally operated in isolation from the broader application security context. This siloed approach has led to missed opportunities for holistic risk management. The integration of Container scanning with Active ASPM breaks down these silos, fostering a more integrated and practical approach to managing security risks across the entire application stack.
Conclusion
The integration of container scanning marks a significant advancement in the field of vulnerability management. Organizations can enhance their security posture in a landscape increasingly dominated by containerized applications by providing contextual analysis, streamlining triage and prioritization, and automating the response to vulnerabilities. Breaking down the silos between container security and source code analysis paves the way for a more comprehensive, efficient, and practical approach to securing applications against the ever-evolving threat landscape.
Start a free trial today to try container scanning in the OX Active ASPM Platform.






)
