“I fail to comprehend the rationale behind labeling them as secrets when, time and again, my developers persist in embedding them openly in the code,” remarked the CISO upon learning about yet another undisclosed secret integrated by the development team into an internet-exposed application, complete with admin permissions, no less. Does this sound familiar to you?
The presence of “secrets” and Personally Identifiable Information (PII) within codebases frequently escapes notice until it reaches a critical point. To adversaries, discovering such information is akin to hitting the lottery, even if the search requires patience. Once obtained, it provides unrestricted access and is like an open checkbook for your environment. As someone who has seen multiple times, I cannot sufficiently emphasize the dangers inherent in this practice. I have seen the catastrophic consequences for developers and businesses when this goes unnoticed.
The Root of the Issue: Security
At the core of this issue, I find a simple yet frequently overlooked principle: security. When developers embed secrets such as API keys, database credentials, or encryption keys directly into their code, they unintentionally create a treasure trove for malicious actors. Similarly, including PII – customer names, addresses, or social security numbers – in source code or log files exposes sensitive data to unnecessary risk.
A single exposed secret in a public repository can grant an attacker access to vast resources, leading to data breaches, financial loss, and irreversible damage to a company’s reputation. The cascading effect of such an event can be monumental. For instance, an attacker gaining access to a database can lead to a massive leak of PII, resulting in legal battles and loss of customer trust.
In August of 2022, LastPass detected an unauthorized party that accessed portions of the LastPass development environment through a single compromised developer account and took portions of source code and some proprietary LastPass technical information. In December of that year, they confirmed that source code and technical information were exfiltrated. In February 2023, they reported another breach with the credentials stolen from the first attack.
Secrets can appear in many places across the development pipeline where attackers can find and use them for malicious purposes. It is essential to search and detect secrets wherever they are active.
How Secrets Can Unintentionally Infiltrate Your Development Process
Despite the risks I have already laid out, here is a breakdown of how secrets can run amok.
- Version Control Vulnerabilities: Modern development practices involve version control systems like Git. When secrets are committed to these systems, they become part of the permanent history. Even if removed in a later commit, the secret remains accessible in history, creating a lingering vulnerability.
- Access Control Neglect: Code repositories often have multiple contributors. Each contributor with access to the codebase potentially has access to all embedded secrets, which increases the risk of internal misuse or accidental exposure.
- Deployment Risks: When code moves from development to production, the embedded secrets go with it. This uniformity across environments can lead to higher risks, significantly if the production environment is compromised.
What About the Perils of PII in Code
Inadequate handling of Personally Identifiable Information (PII) in your software development process can also lead to consequences, ranging from compliance violations with regulations like GDPR and HIPAA to privacy breaches and increased vulnerability to cyberattacks.
- Compliance Violations: Regulations like GDPR and HIPAA have stringent requirements for handling PII. Storing PII in code can easily lead to compliance violations, resulting in hefty fines and legal repercussions.
- Privacy Breaches: Accidental exposure of PII can lead to privacy breaches, affecting individuals whose data was mishandled. This can damage the trust and credibility of a company.
- Target for Cyber Attacks: Including PII in code makes your application a more lucrative target for cyberattacks, as attackers are always looking for easy access to sensitive data.
A Call to Action for Secure Development Practices
Several key strategies must be embraced in cultivating a proactive security posture for your software development. From fostering education and awareness among developers to implementing best practices, conducting regular audits, adopting a security-first mindset, and ensuring continuous improvement, the proactive detection and mitigation of secrets and PII in code, open source, and containers are imperative components of a comprehensive security approach.
- Education and Awareness: Developers must know the risks of embedding secrets and PII in code. Awareness is the first step towards prevention.
- Implementing Best Practices: Use environment variables, configuration files, and secret management tools to handle secrets securely. Encrypt PII and ensure it is never hardcoded into the code.
- Regular Audits and Monitoring: Perform regular code audits and use automated tools to detect the presence of secrets or PII in code repositories.
- Adopting a Security-First Mindset: Security should be a priority from the onset of a project, not an afterthought.
- Continuous Improvement: The field of cybersecurity is always evolving. Stay updated on the latest security practices and tools.
On top of all that, you must actively search and detect secrets and PII in code, open source, and containers before they are deployed. You also need to mitigate the potential damage of exposed secrets.
How to keep your secrets and PII – Secret
The issue of embedding secrets and PII in code is not just a technical problem but a critical business concern. It requires a concerted effort from all stakeholders in the software development process. As we progress into an era where data breaches are becoming increasingly common, we must adopt secure coding practices.
Developing software without including secrets (like API keys, passwords, etc.) or Personally Identifiable Information (PII) in the code is crucial for maintaining security and privacy. Here are some best practices to follow:
- Environment Variables: Store secrets in environment variables instead of hardcoding them in your source code. This way, the secrets are not exposed in your codebase and can be easily changed without modifying the code. For example, in a Node.js application, you can use process.env.YOUR_SECRET_KEY to access an environment variable.
- Configuration Files: Use configuration files not checked into your version control system (like Git). For instance, you can have a config.json file for local development and use .gitignore to ensure it’s not uploaded to your repository. Use a secure method to provide these configuration files or settings in production.
- Secrets Management Tools: Utilize tools specifically designed for managing secrets. These tools provide secure storage and access to secrets, often with auditing and access control features.
- Use Secure Protocols: Always use secure, encrypted protocols like HTTPS to transmit sensitive data, ensuring that data in transit is protected against eavesdropping and man-in-the-middle attacks.
- Access Controls: Implement strict access controls to your code repositories and deployment environments. Only authorized personnel should have access to areas where secrets or PII might be managed.
- Regular Audits: Audit your codebase and environments for accidentally committed secrets or PII.
- Data Encryption: Encrypt PII and sensitive data at rest and in transit. Ensure the encryption keys are securely managed and not hardcoded in the source code.
- Education and Policies: Educate your development team about not including secrets and PII in the code. Implement clear policies and guidelines on how to handle sensitive information.
- Use Tokens and OAuth: Using tokens (like JWT) and OAuth for authentication and authorization rather than passing credentials directly.
- Logging and Monitoring: Be cautious with logging and monitoring. Ensure that logs do not accidentally capture sensitive information. Employ monitoring to detect any unauthorized access or anomalies in the use of sensitive data.
- Code Reviews: Implement a code review process where peers check for accidental inclusion of secrets or PII in the code.
Detecting and Removing Secrets with OX Security
Secrets and PII within code pose a severe threat that often goes unnoticed until it reaches a critical point. As evidenced by real-world breaches, the consequences can be catastrophic, ranging from compliance violations and privacy breaches to increased vulnerability to cyberattacks.
Distinguishing between harmful secrets and those that don’t pose a threat becomes crucial, necessitating robust detection and mitigation strategies. Solutions like OX’s Active ASPM platform offer valuable assistance in actively monitoring policies, responding to security posture issues, and mitigating version control vulnerabilities and access control neglect. Embracing a security-first mindset, staying vigilant through regular audits, and continuous improvement is imperative for a proactive security posture. By adopting secure coding practices and leveraging tools like OX, businesses can automate secret and PII discovery and response, creating a safer digital world for all stakeholders in the software development process.
OX Security’s Active ASPM platform extends across the entire development pipeline, from code to cloud, proactively identifying secrets and PII information. OX empowers users to remediate potential issues before application deployment and exposure by concentrating on the riskiest areas- code and containers.
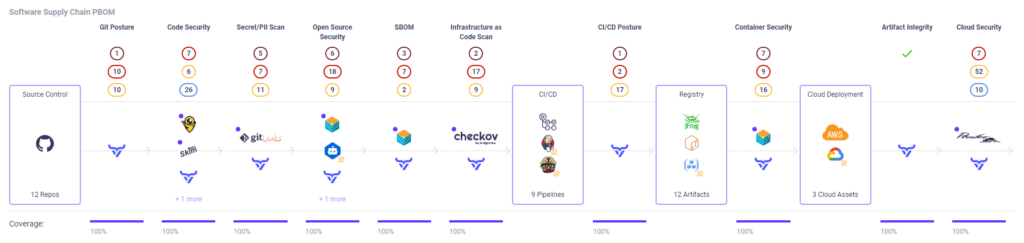
Proactive Mitigation
OX actively monitors policies for Git and CI/CD Posture to respond to security posture issues and mitigate version control vulnerabilities and active control neglect to reduce the damage of an exposed secret.
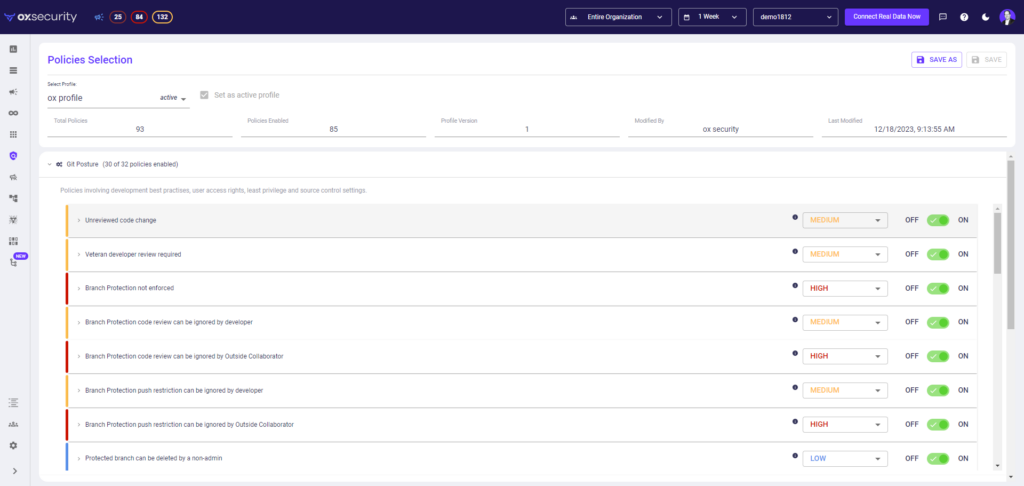
OX also uses its active context sensors to discover secrets in code, open-source packages, and containers. Customers can prevent third-party exposure and deployment risks by remediating secrets and PII before deployment and production.
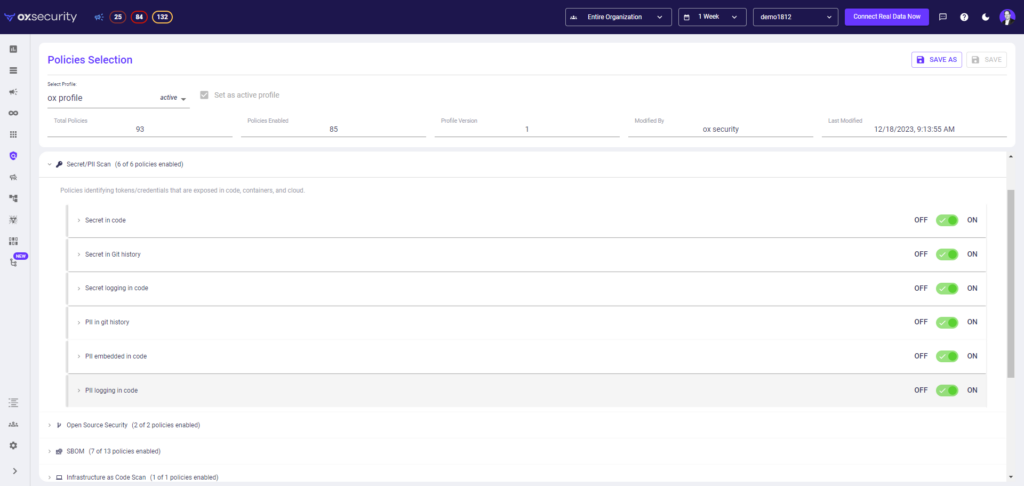
For example, the OX platform can triage and prioritize potentially harmful active secrets. By autonomously discovering secrets throughout the entire software supply chain, OX employs active context sensors to assess the activity and context of each secret, including its association with SaaS applications or exposed containers.
OX’s Automated Secret and PII Discovery for Scalable Protection
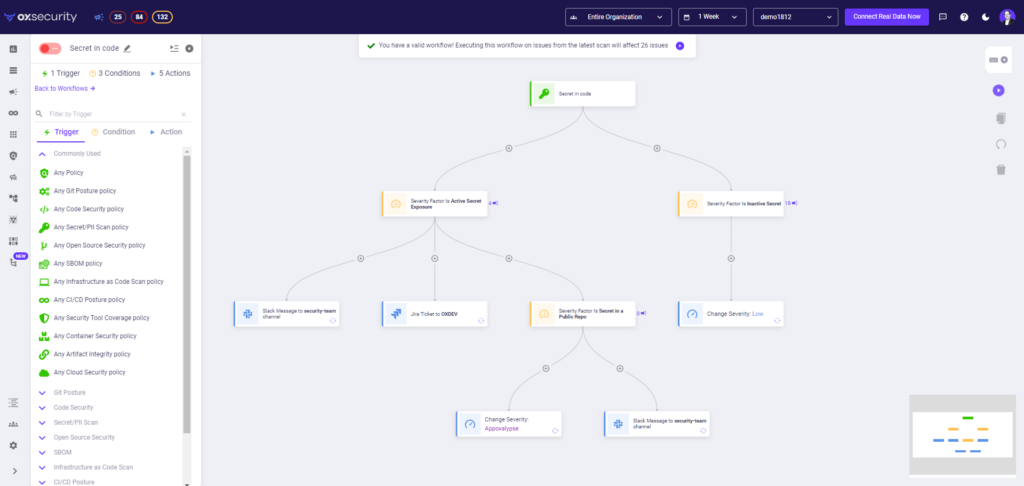
Yes, with OX, you can automate secret and PII discovery and response by creating workflows using our no-code workflow automation to detect and report active secrets and PII before they get exposed.
OX also provides pipeline enforcement capabilities to block the build if a new active secret or PII is inserted and automate the response with ticketing and notifications.
Spill the Code Beans and Check for Secrets with OX
Take the first step towards checking for Secrets. Not sure where to start, schedule a demo and we can show you OX in action and set you up for a trial.