OX for API Exposure Management


Gain full visibility of your APIs with OX’s automated discovery and inventory:
Complete API Cataloging: Automatically discover and inventory all APIs, ensuring an up-to-date catalog that reduces the risk of unmanaged and undocumented APIs.
Hidden API Detection: Detect and manage hidden APIs and SaaS applications, significantly eliminating the risk of unauthorized access that could lead to a data breach.
Continuous Monitoring: Prioritize and mitigate risks as they emerge with OX’s real-time API risk assessments.
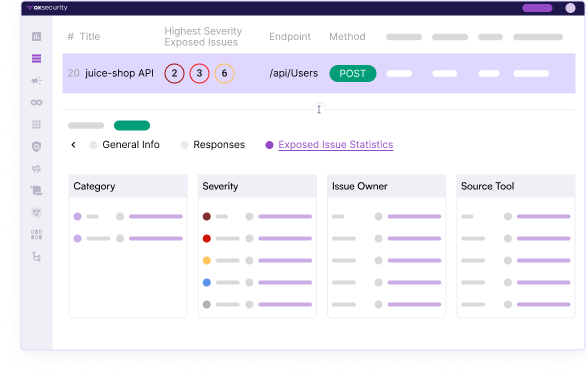
Understand and mitigate your API exposure with OX’s advanced vulnerability linkage:
Direct Vulnerability Linkage: OX connects your APIs directly to known vulnerabilities, offering a clear and actionable view of your API exposure and enabling targeted risk management.
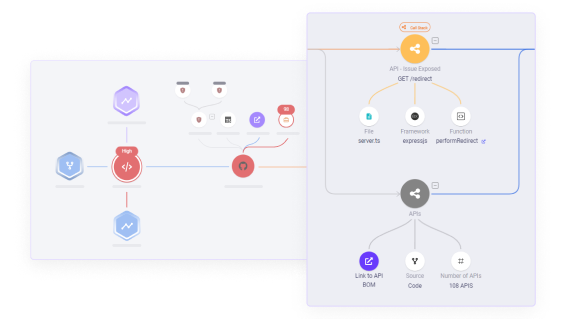
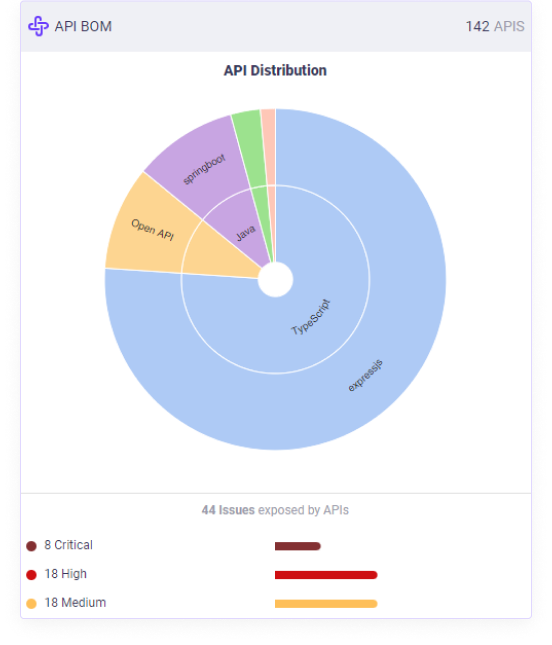
Protect your organization from legal and regulatory risks with OX’s API BOMs:
PII Protection: Prevent the exposure of personally identifiable information (PII) to ensure compliance with legal standards and avoid significant fines and reputational damage.
Regulatory Adherence: Ensure all software components meet legal and regulatory requirements to avoid legal and financial repercussions.
Bake security into your software pipeline. A single API integration is all you need to get started.