Last month, we unveiled our Active ASPM Platform which includes our newest feature, no-code automation workflows. OX has established itself as a frontrunner in automating the discovery, analysis, and prioritization of security risks throughout the entire software supply chain, earning recognition as a Gartner Cool Vendor in platform engineering for scaling application security practices. With these advancements, OX streamlines the process of automating company response protocols for risk identification, enabling businesses to effectively prevent all identified risks from evolving into vulnerabilities—without significant dependence on AppSec teams.
Eliminate vulnerabilities and technical security debt at scale
Application Security (AppSec) teams often grapple with hundreds, if not thousands, of security issues across the software supply chain. Manually investigating each issue without automation requires hours of effort, turning the resolution of each issue into a days-long process. Given the limited resources, organizations tend to address only the top 5% of these issues as a result they risk:
- Exposing themselves to significant vulnerabilities that could jeopardize business operations.
- Validating security too late in the development lifecycle.
- Slowing down release cycles due to lengthy manual triage processes.
- Contributing to escalating technical debt as unresolved issues continue to accumulate.
OX Security provides a solution to these challenges by automating the detection, analysis, triage, and now the response to security issues. This enables AppSec and DevSecOps teams to manage significantly more risks without the need for additional staffing. By reducing the mean time to resolution (MTTR) and preventing critical issues from advancing to production, OX Security helps mitigate the risk of vulnerabilities, streamline release times, and tackle technical debt efficiently.
How to automate your security protocols with OX Security
Creating no-code automation workflows is remarkably straightforward and quick, often taking less than a minute. With a user-friendly visual editor, you can easily set up workflow triggers, apply conditional logic, and specify actions, allowing for customized response flows tailored to your company’s specific protocols.
- Workflow triggers encompass the comprehensive range of policies supported by OX across various security domains, including Git posture, code security, secret scanning, open source security, Software Bill of Materials (SBOM), Infrastructure as Code (IaC), CI/CD posture, container security, artifact integrity, and cloud security.
- Workflow conditions facilitate the execution of diverse actions determined by tailored logic. This logic may hinge on severity, particular programming languages, applications, tags, business priorities, offensive security certification and resilience (OSC&R) tactics, techniques, and more.
- Workflow actions offer the flexibility to choose your response, from sending notifications and creating tickets to opening pull requests (PRs) and blocking the pipeline.
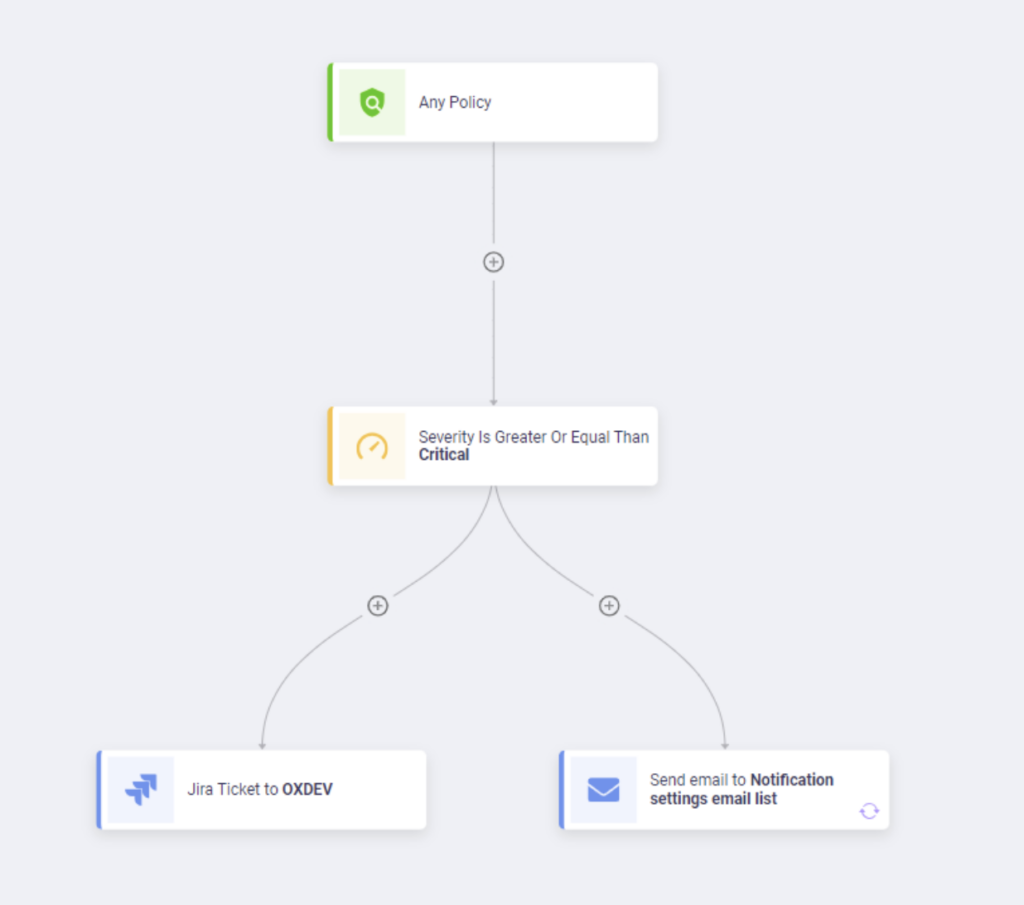
For example, you can build a customized workflow template to automate opening tickets and notifications for any critical policy issue:
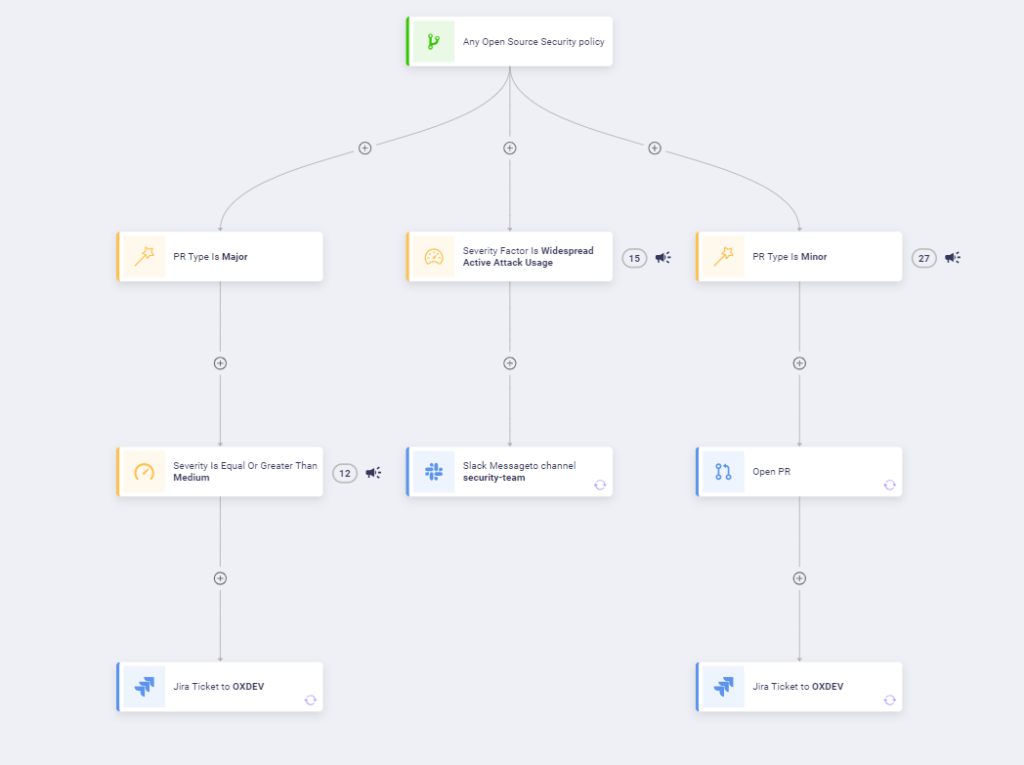
Alternatively, for issues identified during daily code scans, you can set up an automation workflow to automatically initiate a pull request (PR) and notify developers to review and merge it. Such a workflow is designed to address the majority of severe issues, effectively mitigating 80% of the risk.
Really the possibilities which type of workflows you create are endless, some other potential automation workflows include:
- Activating branch protection on all critical repositories without exceptions.
- Automatically preventing security issues from entering the code base by blocking merges.
- Implementing detailed response strategies tailored to the application, programming language, severity of the issue, specific licenses (SBOM), or based on threat intelligence and severity assessments.
No-code security workflow automation enables organizations to address any and all issues automatically, bypassing the need for manual review, analysis, and response. This approach ensures that all identified vulnerabilities are addressed immediately, preventing them from escalating into risks. Furthermore, it allows security teams to start reducing technical security debt efficiently, without the necessity of expanding their team.
Try our no-code automation for streamlined risk management
If your goal is to maximize your existing resources, or you aim to lower technical debt and improve the mean time to resolution (MTTR) for security concerns, we encourage you to explore OX security through our complimentary trial. This trial grants full access to the OX Security platform, encompassing our latest no-code workflow automation feature. Within minutes, you’ll achieve comprehensive risk coverage from code to cloud, effectively prioritize critical issues, and automate response.
Try OX security no-code workflow automation for free