Sprawl happens
Software development organizations evolve. Teams grow. The number of projects increases. Tech stacks change. Technology and management decisions have become more decentralized.
Throughout this evolution, the organization’s AppSec tool portfolio also grows. In dynamic organizations, this can lead to “tool sprawl.” A sprawling AppSec tool portfolio includes many point solutions, acquired by different teams at different times to serve different (or, unknowingly, overlapping) purposes. Sprawling tools result in data silos with different terminology, assignment rules, and resolutions. This situation results in a wasted IT budget, and worse yet, it can make it prohibitively time-consuming to integrate, prioritize, and resolve threats.
If your AppSec tooling is sprawling, and you feel that it has outgrown your ability to manage it effectively, it’s worth investing the time and effort to get it under control. Doing so will help you:
- Gain complete visibility and end-to-end traceability of your software supply chain from the first line of code to production.
- See where there are gaps or overlaps in your security tooling.
- Save money by eliminating tools that don’t yield incremental value.
- Make security an integral part of the development process instead of an afterthought.
- Improve security alerts’ signal-to-noise ratios with automatic triage and prioritization.
- Reduce manual work and automate protective actions, all from a single location.
Here are three ways how OX’s Active ASPM Platform helps to get your AppSec tool sprawl under control so you can maximize protection, productivity, and ROI on your tooling investments:
1: Integrate security alerts to eliminate silos
One of the first problems you want to solve to get a handle on tool sprawl is lack of visibility. That’s why you want to integrate alerts from your tools into a centralized place. Gaining centralized visibility into security issues makes secure development faster and more effective:
- Increase signal-to-noise ratio; focus developers on issues that matter.
- Catch security issues earlier in the development process.
- Reduce raising redundant or untimely security issues.
- Avoid delaying releases by over-prioritizing hygiene issues,
- See related issues across tools that indicate a genuine attack kill chain.
Build vs. Buy
Integrating security issues from your AppSec tools into a central dashboard is a good idea. We see companies try and build these in-house, but the success rate is low. Integrating so many systems is expensive and time-consuming. The faster and more cost-effective path to a centralized view of software supply chain security issues is via a turnkey system. Look for a provider that can give you all of the information you need in one, easy-to-view interface.
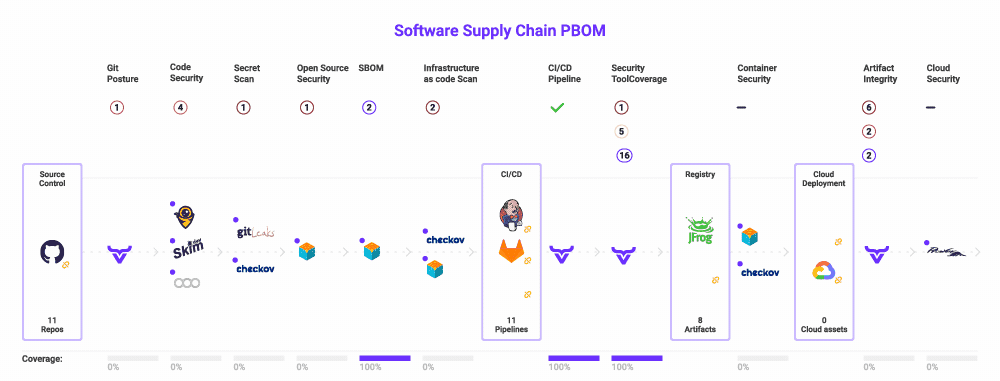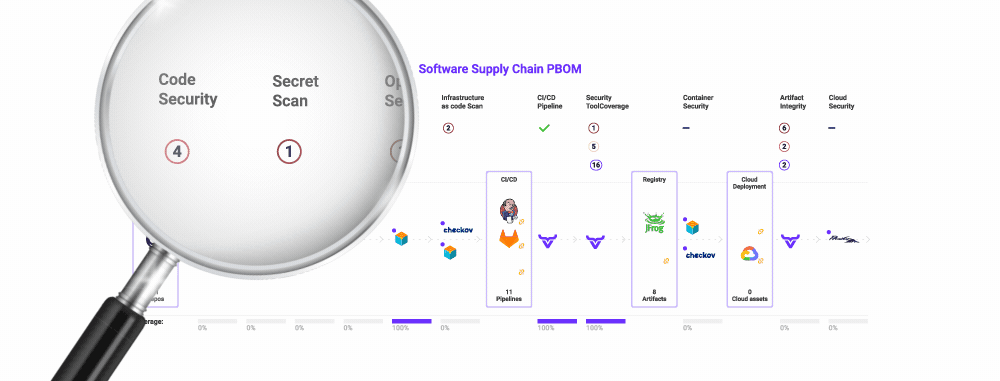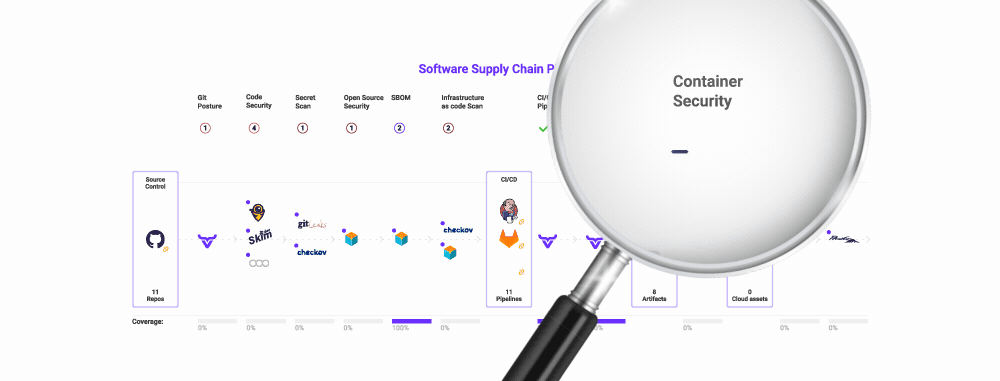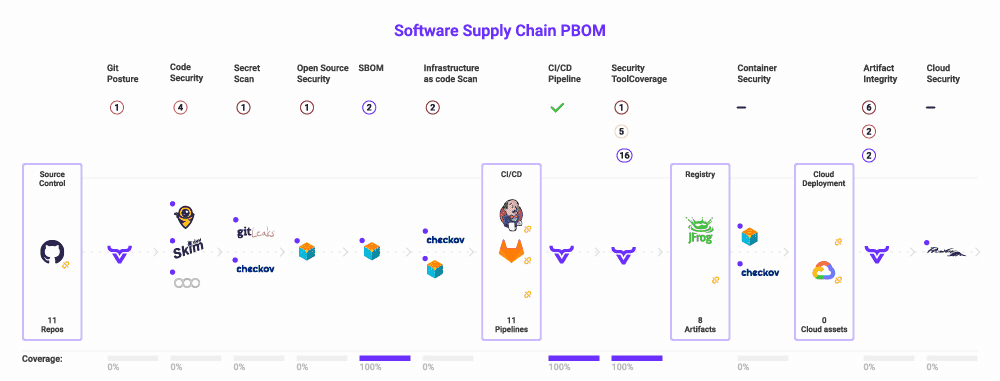
Using our platform as an example, as you can see in the OX dashboard above, thousands of issues from multiple tools for multiple software projects are aggregated and displayed. Whether you build or buy, having this visibility is critically important. It is a prerequisite for the next step in managing security tooling in your software supply chain.
Step 2: Automate issue triage, prevention, and resolution
It’s not uncommon to see thousands of alerts raised by tooling in the software supply chain; it’s so noisy that developers often ignore alerts. Automation can solve the prioritization problem by increasing your alerting signal-to-noise ratio and also automating escalation and resolution for faster, more secure software delivery.
To give you an idea of what’s possible, let’s look at how automation plays an important role in minimizing noise in the environment using OX Security as an example…
Automate issue triage and prioritization
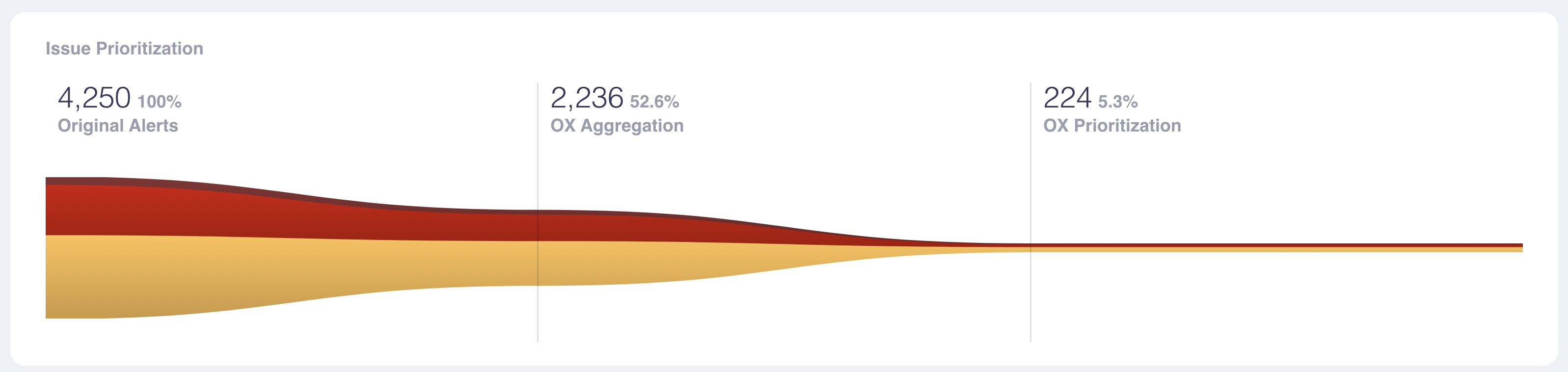
Every time you create a new build, OX produces a knowledge graph for the build that aggregates all of the diverse security issues in your pipeline. OX deduplicates issues and also prioritizes them by their potential business impact. As you can see below, thousands of original alerts are focused down to a few hundred that need the most urgent attention:
The prioritized risks and misconfigurations are organized by OX, using the open-source framework OSC&R for context (more on OSC&R later). This makes the severity and ownership of the issues clearer to everyone. This clarity helps eliminate serious security issues earlier in the development process and also ensures that decisions to block releases for security reasons are well-rationalized and understood by the team.
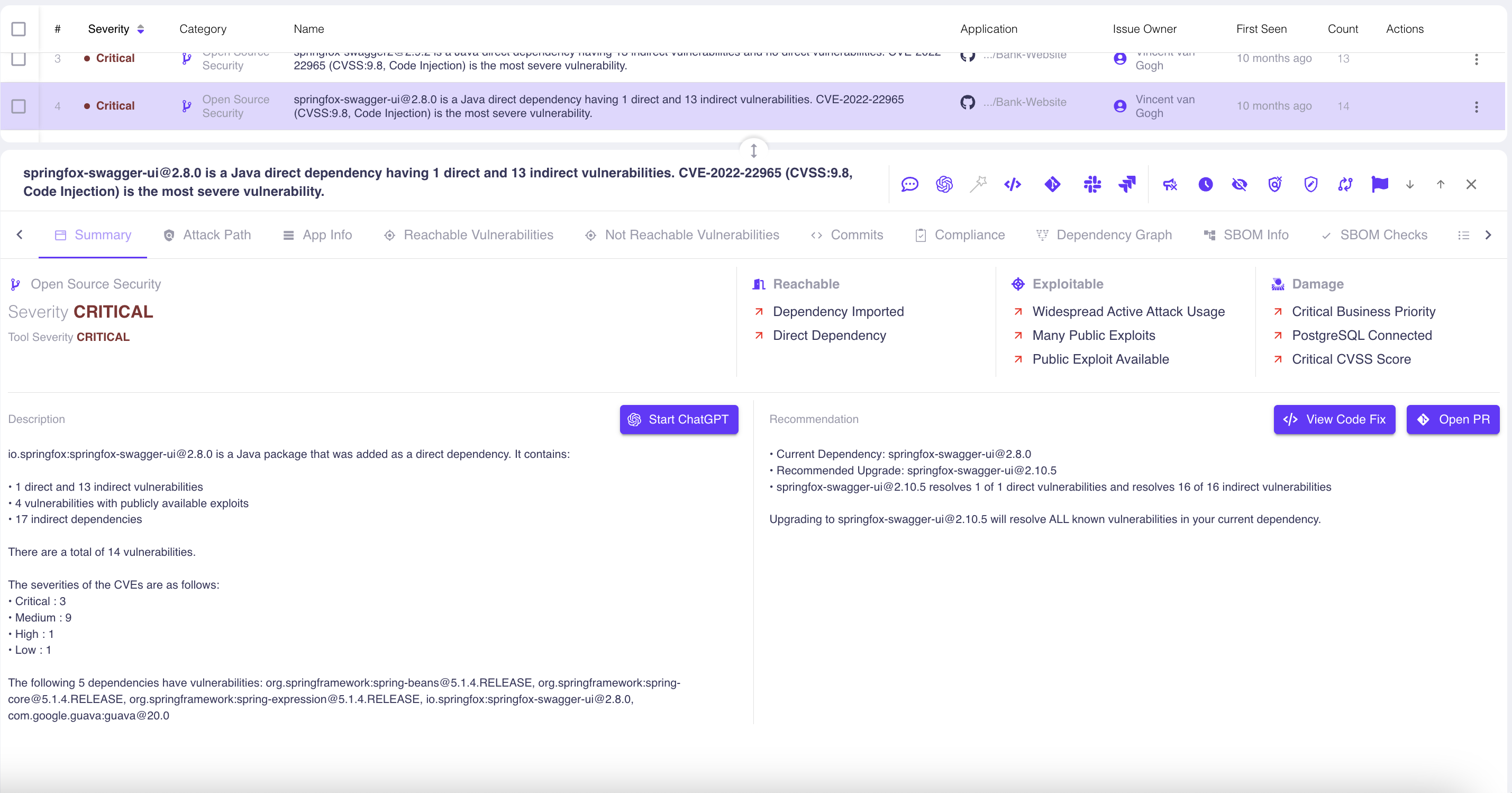
Automate issue resolution and prevention
One of the other problems with security tools sprawl is inconsistent assignment and resolution of issues. A platform like OX solves this by via automated fixes and workflows, and also by providing recommendations and explanations to train and empower your team:
It’s also important to leverage this intelligence during coding and configuration tasks, not just passively after the build process. Look for a platform that integrates into your developers’ IDEs, CI/CD, and other developer tooling to proactively prevent issues. Doing so streamlines your secure development process:
3: Use the OSC&R framework to rationalize your tool portfolio
Lastly, you need to ensure you are using a framework that makes it clear what you need to secure and which threats to watch. If you have this for your entire software supply chain, you can map your existing tools into it, revealing overlap and gaps in your risk coverage.
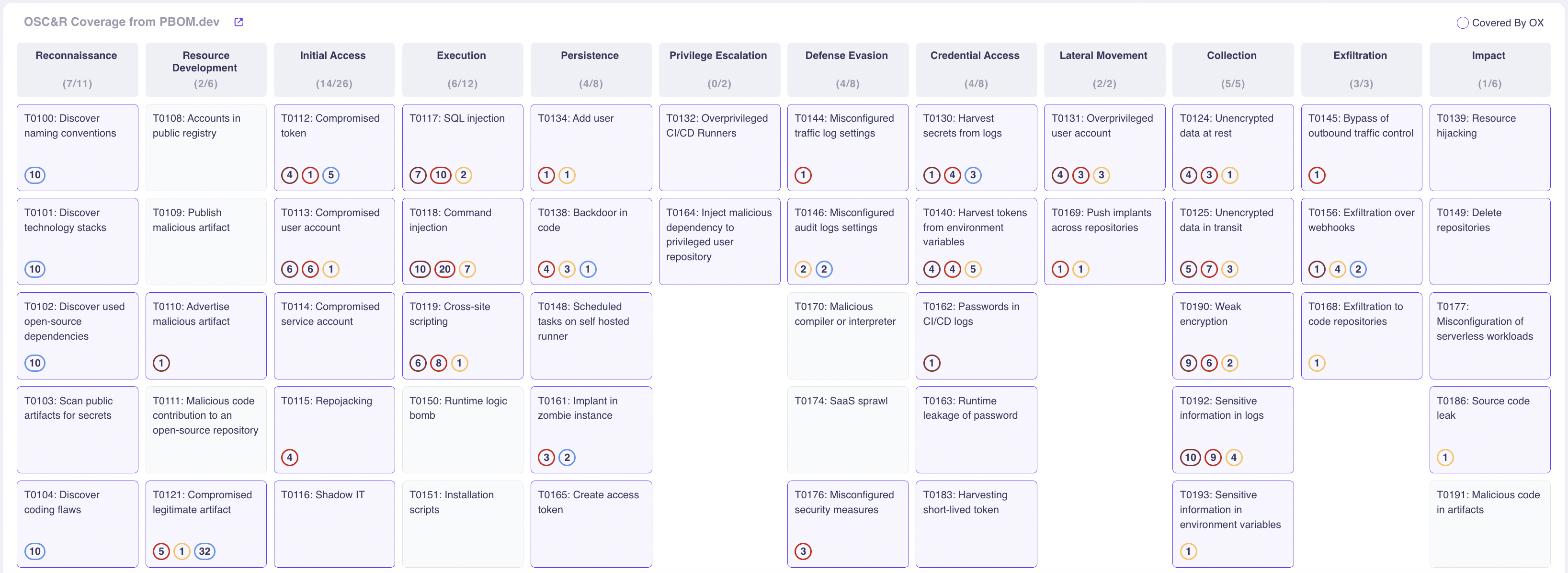
The good news is that this framework already exists. The Open Software Supply Chain Attack Reference (OSC&R) is an industry standard. It does for the software supply chain what Mitre ATT&CK does for endpoint security. As you can see below, OSC&R documents the possible attack points and mechanisms for every part of the software supply chain:
With OSC&R, you can map your AppSec tooling to the threats and make better-informed decisions about which tools to acquire, retain, or end of life. OX Security automates this by scanning your environment and pipelines – from cloud to code. While scanning, OX automatically identifies which tools you are using, and if additional ones should be deployed in order to maximize your coverage. You should now have an AppSec tool portfolio that covers your software supply chain without gaps or overlap.
Get started today
Getting your security tools sprawl under control might sound challenging, but living with it is not an option for modern software teams. OSC&R and intelligence and automation from OX Security can help!
- Try OX Security for free – view your software supply chain coverage and issues
- Contact us to schedule a consultation about improving your software supply chain security.