Today’s cyber-vulnerable world demands proactive strategies to eliminate cybersecurity risks. So why do organizations lack the IT security resources and awareness to tackle security issues?
Over 85% of organizations have witnessed a successful cyber attack in the last 12 months, according to the 2022 Cyberthreat Defense Report. Fines, reputational damage, and business loss are not the only consequences of data breaches. The underlying costs and long-term operational disruption linger long after the bad actors have moved on to the next victim.
The analysis is simple: if security isn’t your top business priority in 2022, you’re putting your organization at risk.
One of the first steps in strengthening your security posture is to assess your cyber risk appetite through a cyber risk score. Eliminating the guesswork could save you huge defamation and revenue losses… and your pride.
Before we learn how to improve your cyber risk score, let’s understand its significance in securing your enterprise and how to calculate it.
What is a Cyber Risk Score?
A cyber risk score identifies IT vulnerabilities, exposed resources, and threats that can potentially lead to security risks or data breaches.
On a macro level, it helps you understand the strength of your security. From this information, you can determine a strategy to assess and prioritize vulnerabilities, protect critical resources and implement cybersecurity frameworks that standardize risk assessment.
Here are some of the most common cybersecurity frameworks.
- NIST Cybersecurity Framework. Considered the gold standard in assessing your cybersecurity strength, NIST was introduced in response to the US Federal Government’s order to improve cybersecurity infrastructure.
- SOC2 (Service Organization Control) Type 2 comprises over 60 compliance requirements and an exhaustive auditing procedure.
- GDPR (General Data Protection Regulation) is arguably the keyword of the decade. This framework requires organizations established in the EU to comply with compliance requirements to secure consumer data and access rights.
How is the Cyber Risk Score Calculated?
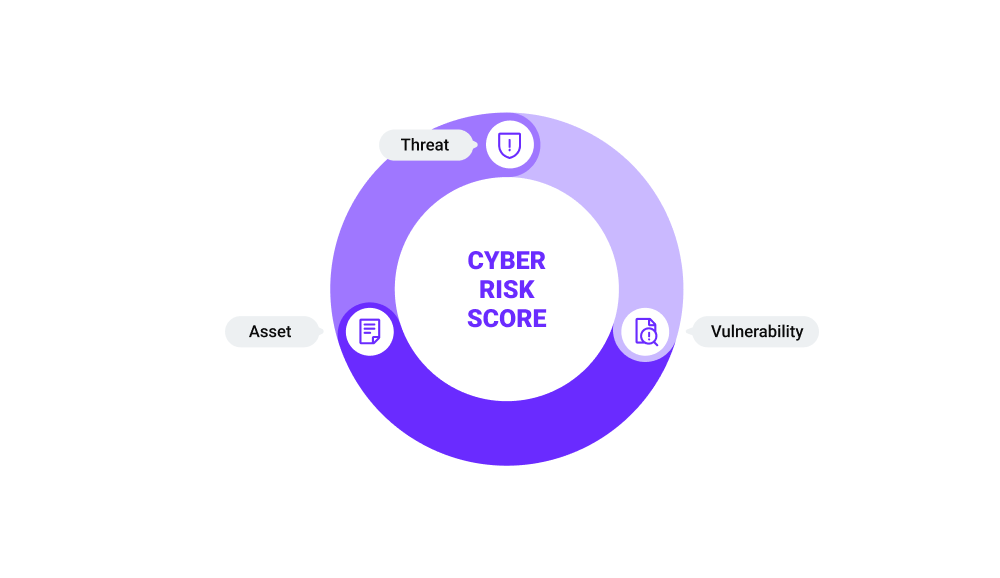
The cyber risk score isn’t strictly a mathematical formula. Rather, it’s an understanding of where your security defenses stand against a threat. Calculate it with the below formula:
Risk = Threat x Vulnerability x Asset
- Threat: A threat or risk such as website outages, espionage, and hacking that could harm your assets or resources.
- Vulnerability: A vulnerability is like a crack in the wall that could allow external and malicious elements to exploit your confidential system.
- Impact: Impact is the measure of the damage your organization will face from a security incident. It could cost you money, data loss, legal ramifications, or service downtime.
- Asset: Assets are IT and data sources that are valuable for enterprises.
Who Should Perform a Cyber Risk Assessment?
Do you intend to achieve resilience against data breaches and cyber-attacks? If so, you must conduct cyber risk assessments.
Your assessment should be a holistic and collaborative process. Encourage your in-house teams to assess performance and actively work on data to understand criticality thoroughly. You can also outsource it to an expert agency.
- What are the Benefits of Cyber Risk Scoring?. Cyber risk scoring means taking complete control of your cyber defenses instead of waiting for an attack to happen. What are some of the benefits of cyber risk scoring?
- Identify the Chinks in Your Armor. By assessing your security position, you can identify vulnerabilities and hidden threats that may have found their way into your environment due to oversight.
- Strengthen your Walls of Security. You can implement strong policies to protect your end-to-end ecosystem by identifying the areas of weakness and exposed assets.
- Verify Third Party Vendors. Gartner states that “cybersecurity ratings will become as important as credit ratings when assessing the risk of existing and new business relationships.”
- Safeguard Your Documents from Breaches. Stealing critical customer data is one of the biggest motivators of cyber attacks. You can mitigate this by securing your documents comprehensively.
- Empower Employees to Avoid Security Traps. Train your employees on cybersecurity best practices to become vigilant to security and avoid any employee-led security challenges.
5 Steps to Improve Your Cyber Risk Score
Cyber threats are becoming more creative and sophisticated, with unique ransomware exploiting deeply embedded and undetected vulnerabilities. Although these new attack trends call for better cybersecurity practices, you can always use the cyber risk score to ensure your security stance is perfect.
Here are some essential tips to improve your cyber risk score to be proactive in managing security risks.
1. Prioritize Risks
Despite your best efforts, trade-offs are unavoidable.
Assessing security and governance standards is often a complex process. It involves transforming the evaluation of your systems into an understandable format and highlighting the most immediate critical risks, which your development teams prioritize.
To improve your cyber risk score, you could adopt a risk matrix and a proper scoring framework that separates risks into high, medium, and low categories. You can also use this risk matrix to communicate the prioritized risks to the concerned teams.
Alternatively, choose a security solution like Ox Security that enables you to manage risks based on priority to meet your business goals.
2. Conduct Employee Training
6 billion phishing attacks will occur this year, with a shocking 30% open rate. Lack of awareness among employees can be a huge cybersecurity risk and affect your cyber risk score.
Phishing attacks disguise malware as harmless links and attempt to access user data. Employees fall prey to these scams because they seem genuine to untrained eyes.
The responsibility falls to organizations and security leaders to train your employees on various forms of security attacks and vulnerabilities—and their disastrous effects. You could begin by teaching best practices like changing their passwords frequently and checking email addresses before opening a mail or clicking on a link. You could also invite a cybersecurity expert as a guest to conduct training sessions or recommend courses.
Register for our ASPM Mastery Webinar.
3. Implement Continuous Monitoring
Despite cloud technology’s operational and IT benefits, it also opens up new avenues for attackers to exploit your systems and lower your cyber risk score.
By implementing automated system observability, you can continuously scan your IT environment to detect hidden threats, alert stakeholders to vulnerabilities, and initiate immediate remediation.
Unlike manual security checks, automation simplifies continuous monitoring and also accelerates response so that you can avoid a threat from becoming an incident. Continuous monitoring requires a systematic approach to identifying data storage, users, and devices and setting tolerance levels. Once you have done this, you can analyze the possibility of a breach and implement risk controls.
Ox Security’s solution gives you total visibility into your security stance across source code, pipelines, artifacts, and applications. It also enables you to monitor your environment continuously to ensure that your software supply chain does not drift from its secure state.
4. Work with Secure Partners and Vendors
Almost all businesses nowadays rely significantly on third-party services and vendors. Gartner reported that about 80% of organizations take a unified approach for their web, cloud services, and private application access.
But this also makes enterprises vulnerable because their security posture depends on vendors. If your partners are vulnerable, your cyber risk score will suffer too. This calls for a robust vendor management strategy.
When selecting a vendor, you must ensure that their policies or attitudes won’t impact your operations, compliance requirements, and business objectives. You can work these out by implementing a robust selection, onboarding, and monitoring strategy.
5. Protect Your Software Supply Chain
A significant portion of any enterprise software today comprises open-source or third-party codebase. The vulnerabilities these open-source codes possess are then transferred into your software, paving the way for supply chain attacks. Since integrating third-party code requires you to grant access to sensitive data, it becomes all the more critical for you to limit the attack surface.
The US Government’s latest executive order stressed the importance of improving supply chain security caused by third-party software updates, malware, and application installers. Besides open-source code, you’ll also need to limit integration with assets that restrict your control, such as IoT, cloud applications, and social media.
Prepare for Cybersecurity Threats with Enhanced Monitoring and Prioritization
Cybersecurity is hands-down the biggest challenge of this software era. Almost every organization, big and small, is falling prey to malicious attacks. With these attacks getting more unique and complex, it’s crucial to get your basics right. You can do this by efficiently assessing your IT security posture and using cyber risk scoring to determine the best risk management strategy.
To ensure that you implement a robust and resilient cybersecurity strategy that includes key features like continuous monitoring and risk prioritization, you can use a DevSecOps solution like Ox Security. It automates monitoring and observability of every aspect of your software supply chain to integrate everything and reduce manual work.
Try for free or request a demo.






)

