Transitive dependencies are one of the biggest headaches software developers must manage. Relationships between software components are complex (to say the least) and specifically for transitive dependencies — that is, indirect relationships between software components — finding and understanding the impacts can be both time-consuming and tricky. Nonetheless, the ability to trace transitive dependencies and their potential vulnerabilities (i.e., transitive vulnerabilities) is critical to building functional and reliable software and ensuring AppSec teams can find and fix major issues before software is put into production and widely used.
Last week, during the 2024 OWASP Global AppSec conference in Lisbon, OX Security researchers Eyal Paz and Liad Cohen shared some of OX’s latest research on the impacts of transitive vulnerabilities and demonstrated how AppSec practitioners can start to take a more effective approach to managing them. Here, we include a summary of their findings.
The Challenge with Transitive Dependencies
Transitive dependencies complicate security assessments, as they may not be immediately visible to or manageable by developers. It’s this hidden nature that necessitates the use of automated tools and comprehensive scanning technologies that can unearth indirect dependencies and help security teams analyze, prioritize, and minimize potentially harmful vulnerabilities that could leave applications — and their users — open to heightened risk.

The Overlooked Risks of NPM Install Outputs
Package managers like NPM are common tools for software development. They display vulnerability warnings during installation processes, and can help developers triage issues. However, given the number of alerts that could result from using an NPM, developers have increasingly become desensitized to these warnings, often ignoring them due to the perceived irrelevance of the vulnerabilities on their immediate project needs. This behavior is risky, as it parallels the fable of “The Boy Who Cried Wolf,” where constant alerts are ignored until a real threat materializes and potentially leads to more-severe consequences.
Exploring Open Source Vulnerability Exploitation
The possibility of exploited vulnerabilities in open-source dependencies is a crucial concern for AppSec professionals. For instance, a well-maintained project like P server, which started under Facebook’s stewardship before becoming completely open sourced, shows how a single unpatched vulnerability can lead to a Denial of Service (DoS) attack. This example, as well as many others like it, highlights the necessity of continuous monitoring and updating of transitive dependencies throughout the SDLC, not just the direct ones.
A Structured Approach to Assessing Security Risks
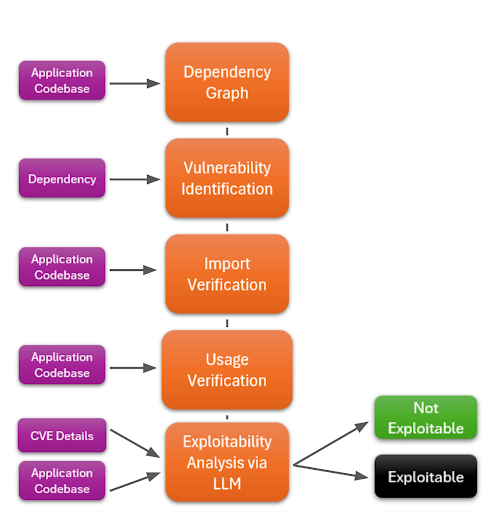
To understand and analyze the security risks associated with transitive dependencies, it’s helpful to take a methodical approach This process involves:
- Dependency Graph Construction: Visuals are a simple way to understand how entities in an environment are interconnected, especially when it comes to distant relationships. Building a dependency graph based on manifest files that maps out all connections between software components and related vulnerabilities, including transitive ones, will help highlight where developers and security teams need to take action.
- Vulnerability Correlation: AppSec teams need to see the big picture when it comes to remediating software-based issues. This requires not just finding and associating each dependency with known vulnerabilities, but also taking their severity into account and prioritizing mitigation based on the overall business requirements.
- Code Usage Validation: False positive and false negatives are a major reason developers tend to ignore typical AppSec tools. It is therefore critical to have the means to ensure that found dependencies are actually used in the code, which helps teams assess their relevance and potential impact.
- Exploitability Analysis: Developers and AppSec teams cannot hope to triage every software vulnerability associated with their codebase — hundreds could exist for every project. As such, it is pertinent to determine which vulnerabilities are exploitable in the context of how they are implemented in an application.
- Final Assessment: Advanced tools like LLMs can help analyze whether usage patterns in code meet the conditions necessary for a vulnerability to be exploitable, and allow AppSec pros to move more quickly and accurately in finding and acting upon the highest priority vulnerabilities.
Methodology
Probabilistic and Statistical Approaches to Security
Given the complexity and volume of dependencies that comprise modern applications, it is recommended to use a probabilistic approach to evaluating the likelihood of vulnerability exploit. This involves using statistical methods that consider the depth of each dependency and apply a decay factor to assess the diminishing impact of vulnerabilities buried deeper within the dependency tree.
Effective Mitigation Strategies
Because not every cybersecurity risk can be eliminated, teams should consider a multi-pronged strategy for mitigating transitive dependency risks, including:
- Virtual Patching: Implement security measures that do not require actual code changes but rather shield the application from potential exploits.
- Proactive Rebuilding: Regularly update and rebuild applications to include the latest patches and dependency versions.
- Custom Patching: For unpatched vulnerabilities, especially in unmaintained projects, create and apply custom patches that can help harden applications against potential exploits.
Conclusion
Understanding and managing transitive dependencies (and their transitive vulnerabilities) must be baked into the software security lifecycle; otherwise, critical issues that threaten both the proper functioning of applications and the security of their users is inevitable . As such, developers and security teams must move beyond the status quo in AppSec and deploy modern scanning techniques that illuminate the entirety of the application, from initial build to its use in production. This means not only understanding all components that make up an application, but how all the pieces fit together, from direct relationships and dependencies to the transitive dependencies and vulnerabilities that could introduce unforeseen problems.
With an awareness of and focus on transitive dependencies, AppSec teams can proactively manage security risks in software development and ensuring that applications are safe from the potentially devastating impacts of overlooked vulnerabilities.