OX Research Maps Most Common Supply Chain Vulnerabilities to Attacker TTPs
For our recent threat research report, OSC&R in the Wild: A New Look at the Most Common Software Supply Chain Exposures, we analyzed over 100,000,000 software supply chain alerts and mapped the most serious vulnerabilities to OSC&R, the first-of-its-kind threat matrix of TTPs used in cyber attacks on software supply chains. If you missed our previous blog summarizing the findings, check it out here.
One of the primary goals of this research was to identify the tactics that could exploit the most commonly found supply chain vulnerabilities in order to provide AppSec, DevOps, and Product Security teams with a better understanding of how and where adversaries are most likely to attack their software supply chain. With that in mind, we are focusing this blog on the 10 TTPs that posed a risk to the greatest number of applications in our dataset of nearly 140,000 applications.
Top 10 Most Common TTPs Based on the OSC&R Software Supply Chain Attack Matrix
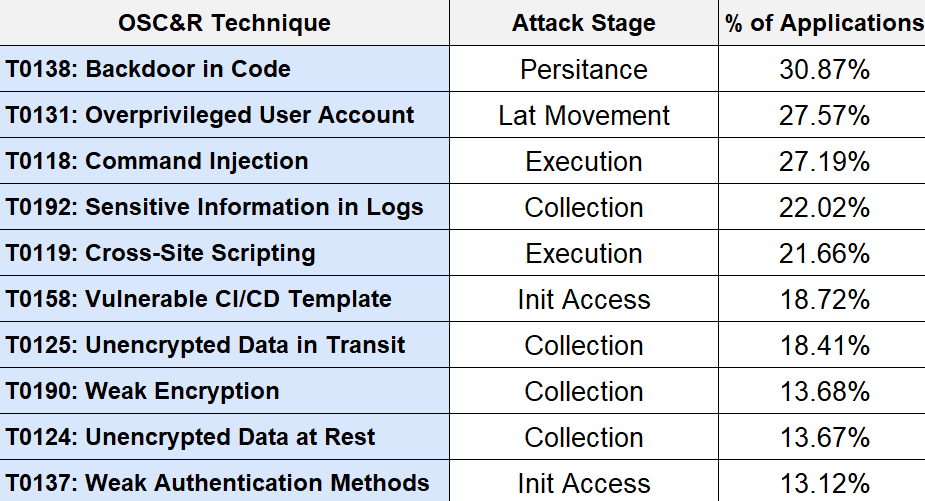
Several interesting points stand out in the stack-ranked list of TTPs above.
Top tactics span across five key stages of the OSC&R attack matrix
Five of the 12 attack stages in the OSC&R matrix (see below) are represented in the top 10 tactics. From early stages such as Initial Access and Execution, to later stages such as Lateral Movement and Collection, we frequently saw vulnerabilities which could be exploited across the kill-chain.
Attack techniques highlight urgent need for enhanced data security in enterprise applications
Though there were a variety of attack methods represented, 4 of the top 10 techniques — T0192: Sensitive Information in Logs, T0125: Unencrypted Data in Transit, T0190: Weak Encryption, and T0124: Unencrypted Data at Rest — are linked to the exploit of poor data security practices. This shows an urgent need to improve the protection of sensitive and exploitable data within application code. Absent or poor encryption, and exposure of data such as personally identifiable information (PII) data, tokens, credentials, and internal system information, can create an easy path for adversaries to gain access to enterprise applications and networks.
The rise of TO138 backdoor exploits in code
The prevalence of vulnerabilities exploitable by TO138: Backdoor in Code is particularly concerning. Attackers have been exploiting vulnerabilities to insert malicious backdoor code for more than 25 years. Yet the recently discovered CVE-2024-3094 exploit, which targets XZ Utils, a widely used package present in major Linux distributions, makes it clear that adversaries are still successfully targeting this attack path. With the prevalence of these vulnerabilities in our code sample, it’s not hard to understand why.
Final Thoughts:
Many of the most commonly observed vulnerabilities are tied to fairly fundamental security controls such as authentication, encryption, publicly available information in logs, and the principle of least privilege. Application security can be very complex, but these findings serve as a reminder not to overlook the basics when developing your AppSec strategy.
Download the full OSC&R in the Wild: A New Look at the Most Common Software Supply Chain Exposures report here.
For information on how OX can help detect and reduce software supply-chain risk, schedule a call with one of our application security experts.









